PortSwigger - Business Logic Vulnerabilities - Lab 2
Lab 2 - High-level logic vulnerability
Lab Objective:
This lab doesn’t adequately validate user input. You can exploit a logic flaw in its purchasing workflow to buy items for an unintended price. To solve the lab, buy a “Lightweight l33t leather jacket”
You can log in to your own account using the following credentials:wiener:peter
Reference:
Port Swigger - Lab 2
Rana Khalil - Business Logic Vulnerability - Lab2
Python Script
Solution
1. Login in with provided credentials wiener:peter
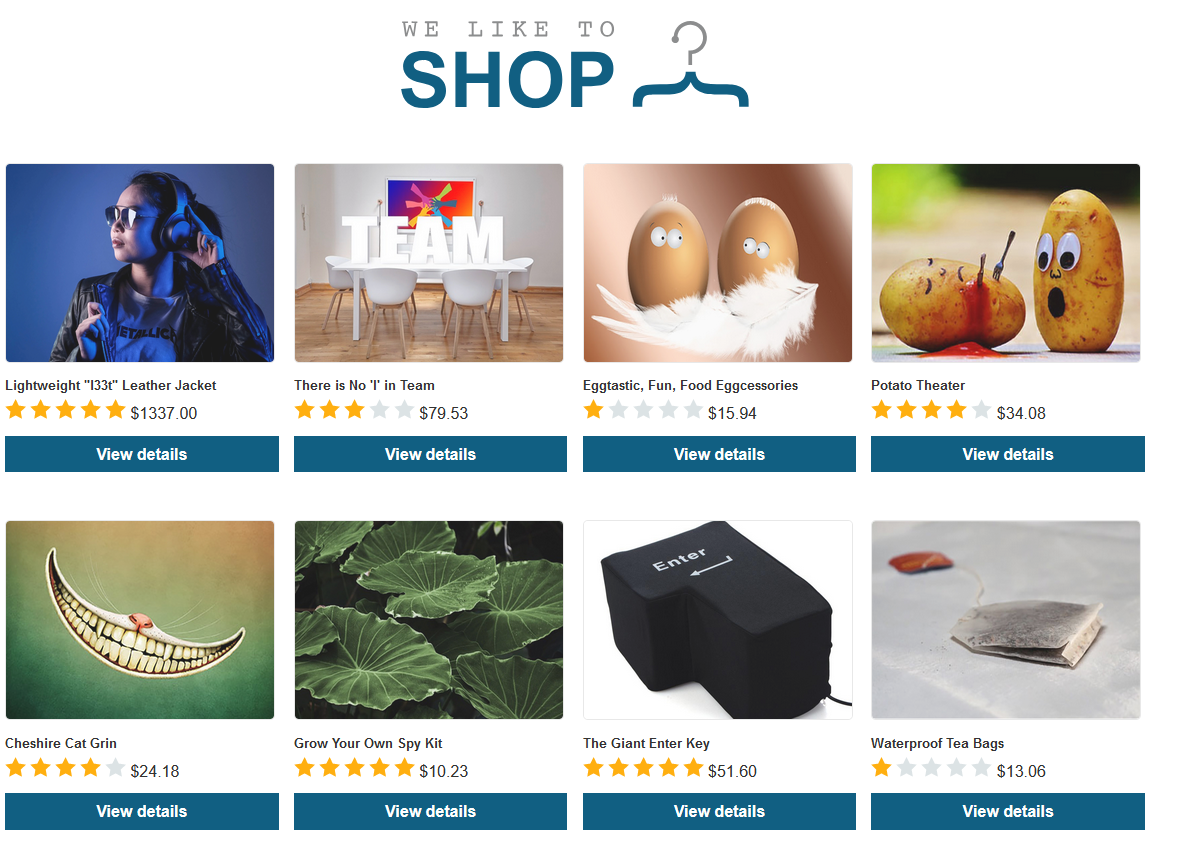
2. Click on Home to see the shop.
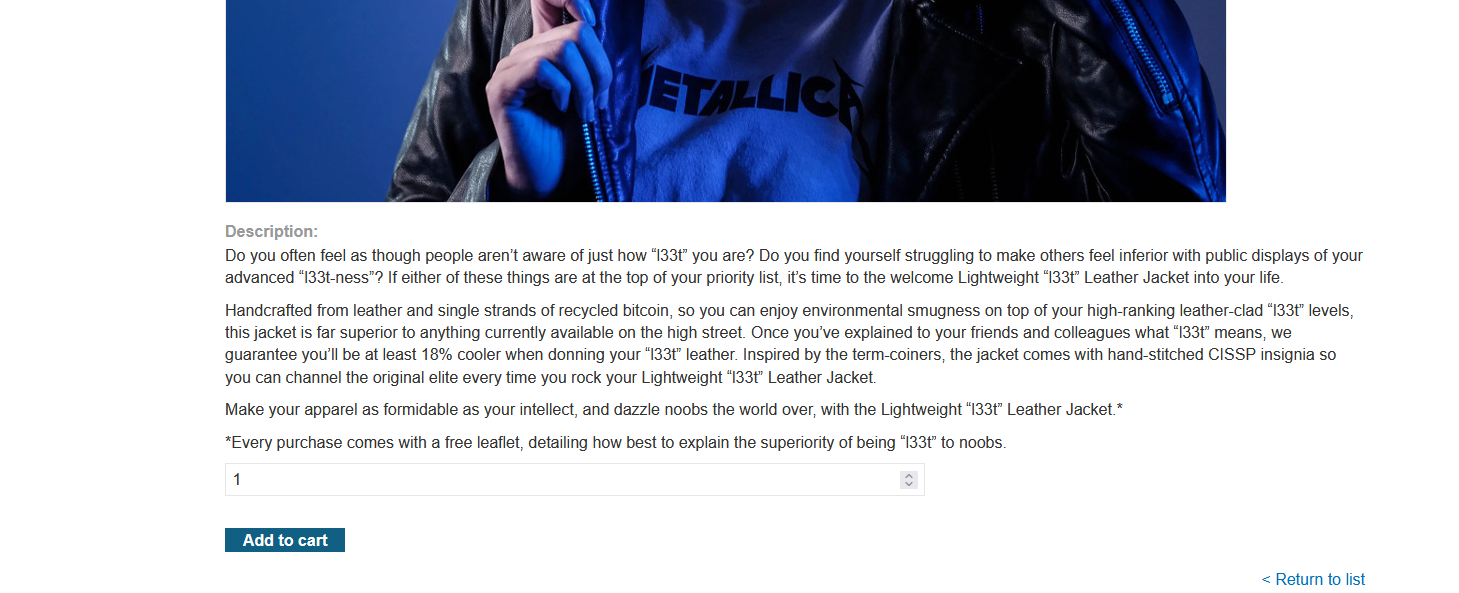
3. Click on view Details for the Lightweight "l33t" Leather Jacket product
4. Add Lightweight "l33t" Leather Jacket to your cart.
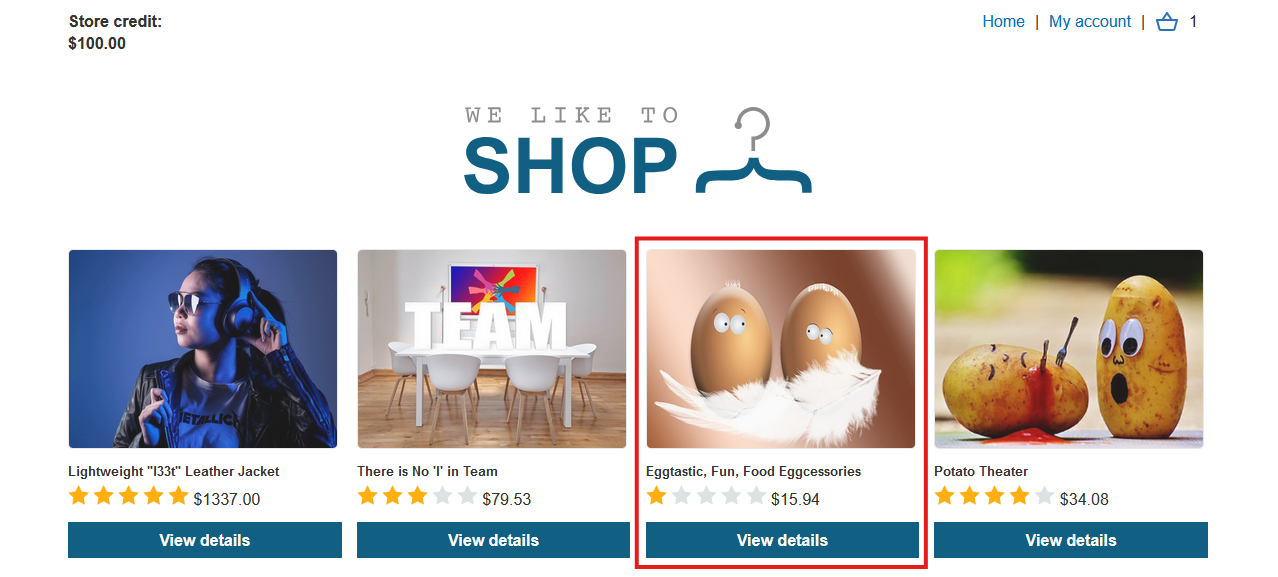
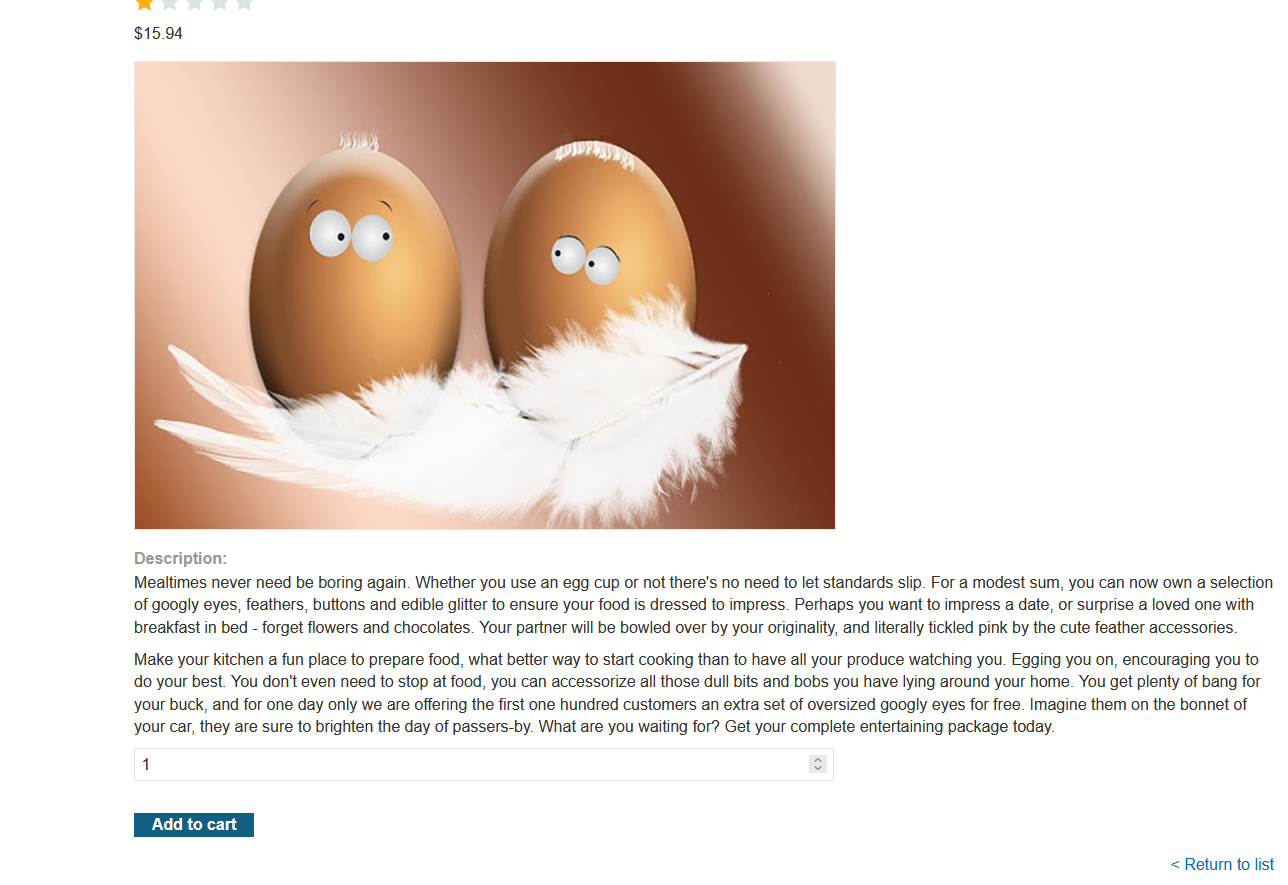
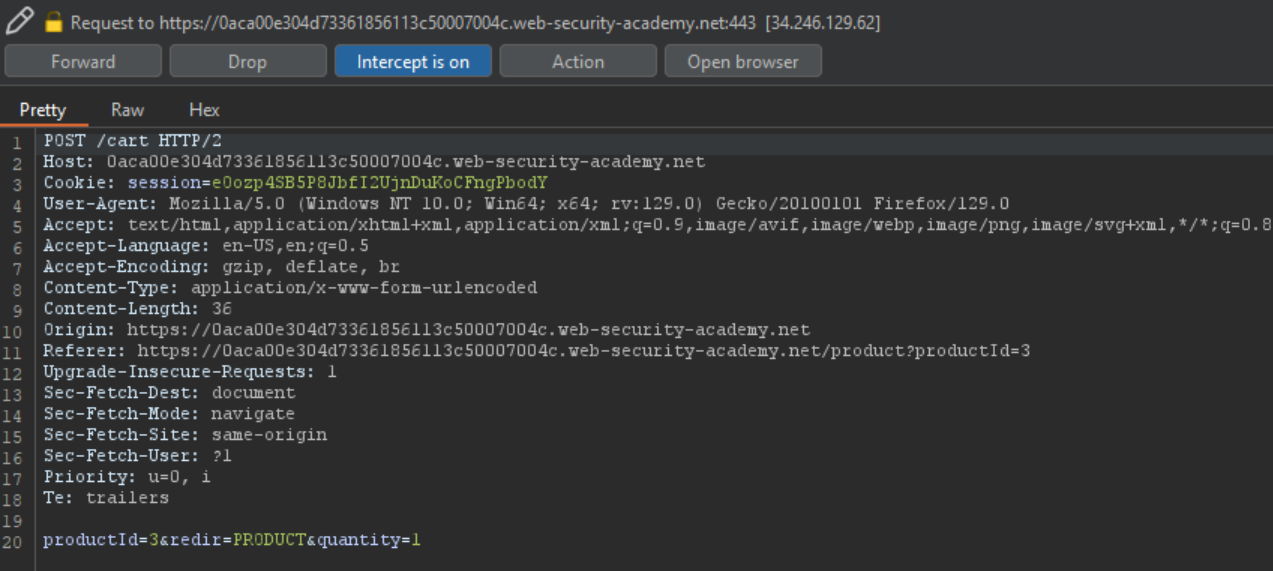
5. Add another item Eggtastic, Fun, Food Eggcessories to your cart and intercept the request
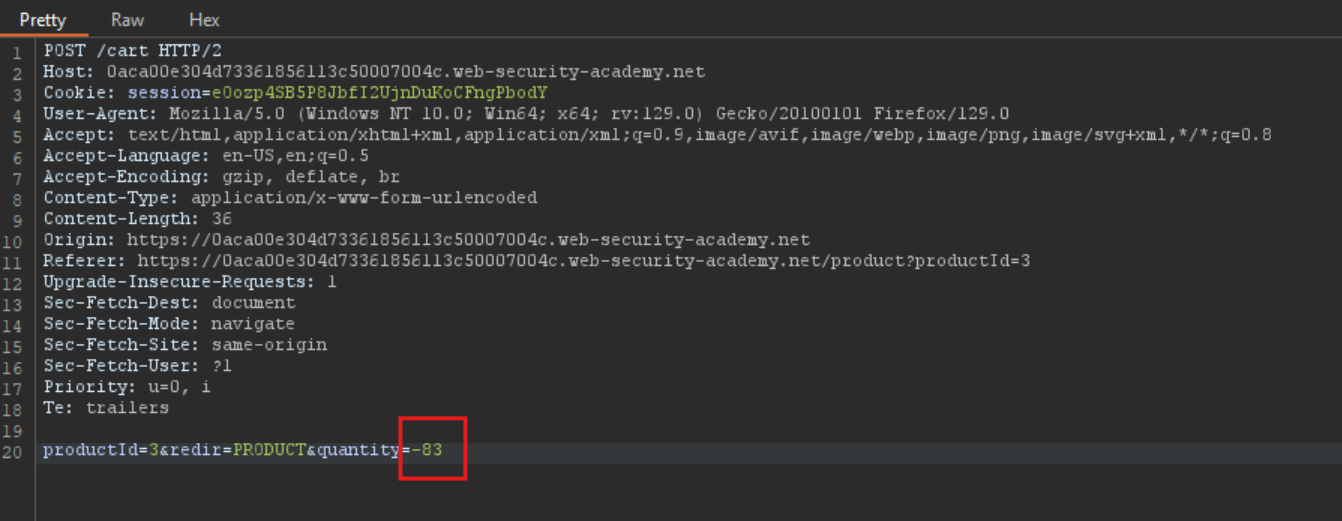
6. Change the quantity value to -83
This will add a negative value of 15.94 * -83 = $1323.02 to our cart
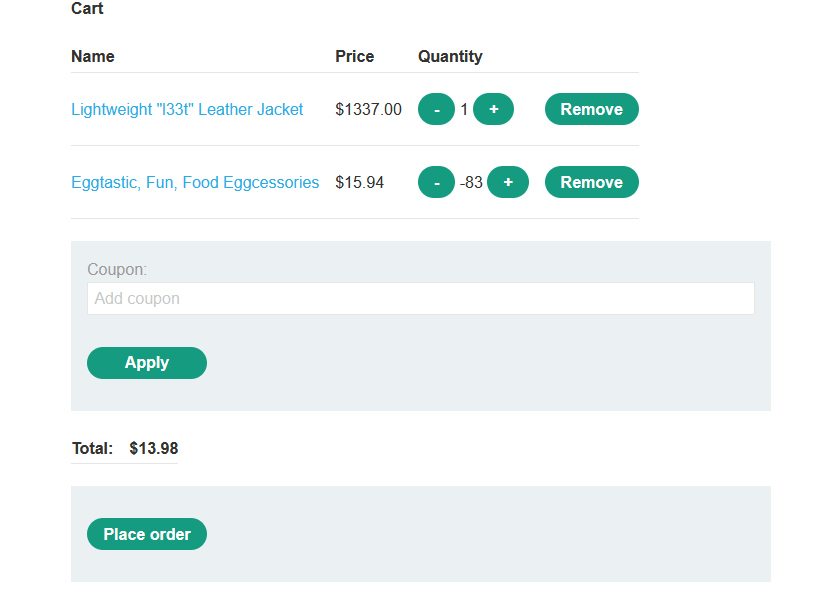
7. Navigate to your cart and notice the total amount for the order is $13.98
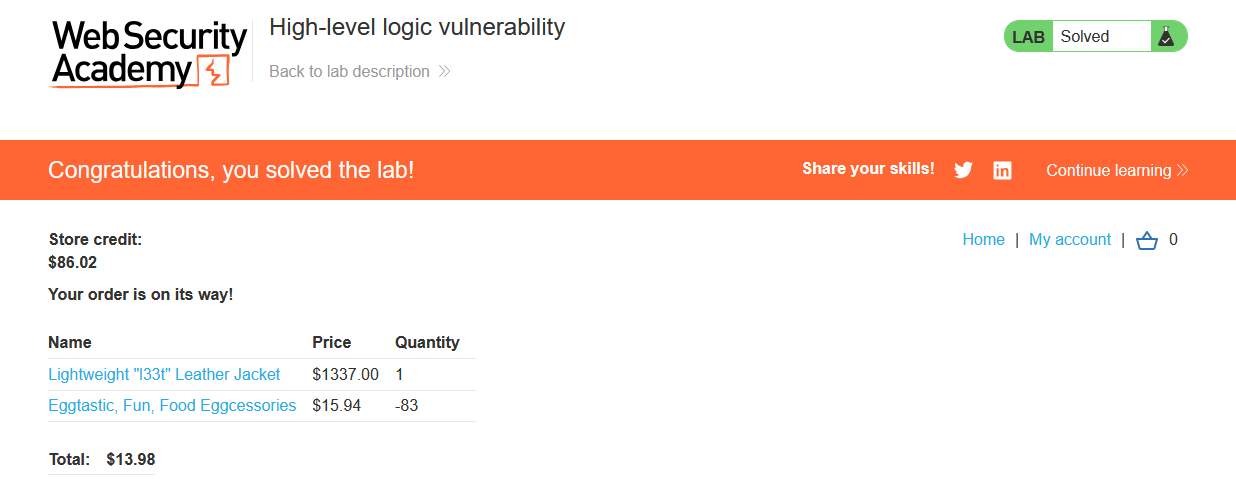
8. Click on Place Order we’ve now purchased the Lightweight "l33t" Leather Jacket for $13.98
This post is licensed under CC BY 4.0 by the author.