Hack The Box - Academy - Javascript Deobfuscation Skills Assessment
Explore this detailed walkthrough of Hack The Box Academy’s Javascript Deobfuscation module. Learn effective techniques to decode obfuscated scripts.
Overview:
You are given an online academy’s IP address but have no further information about their website. As the first step of conducting a Penetration Test, you are expected to locate all pages and domains linked to their IP to enumerate the IP and domains properly.
Finally, you should do some fuzzing on pages you identify to see if any of them has any parameters that can be interacted with. If you do find active parameters, see if you can retrieve any data from them.
Links:
Javascript Deobfuscation
Javascript Deobfuscation - Cheat Sheet
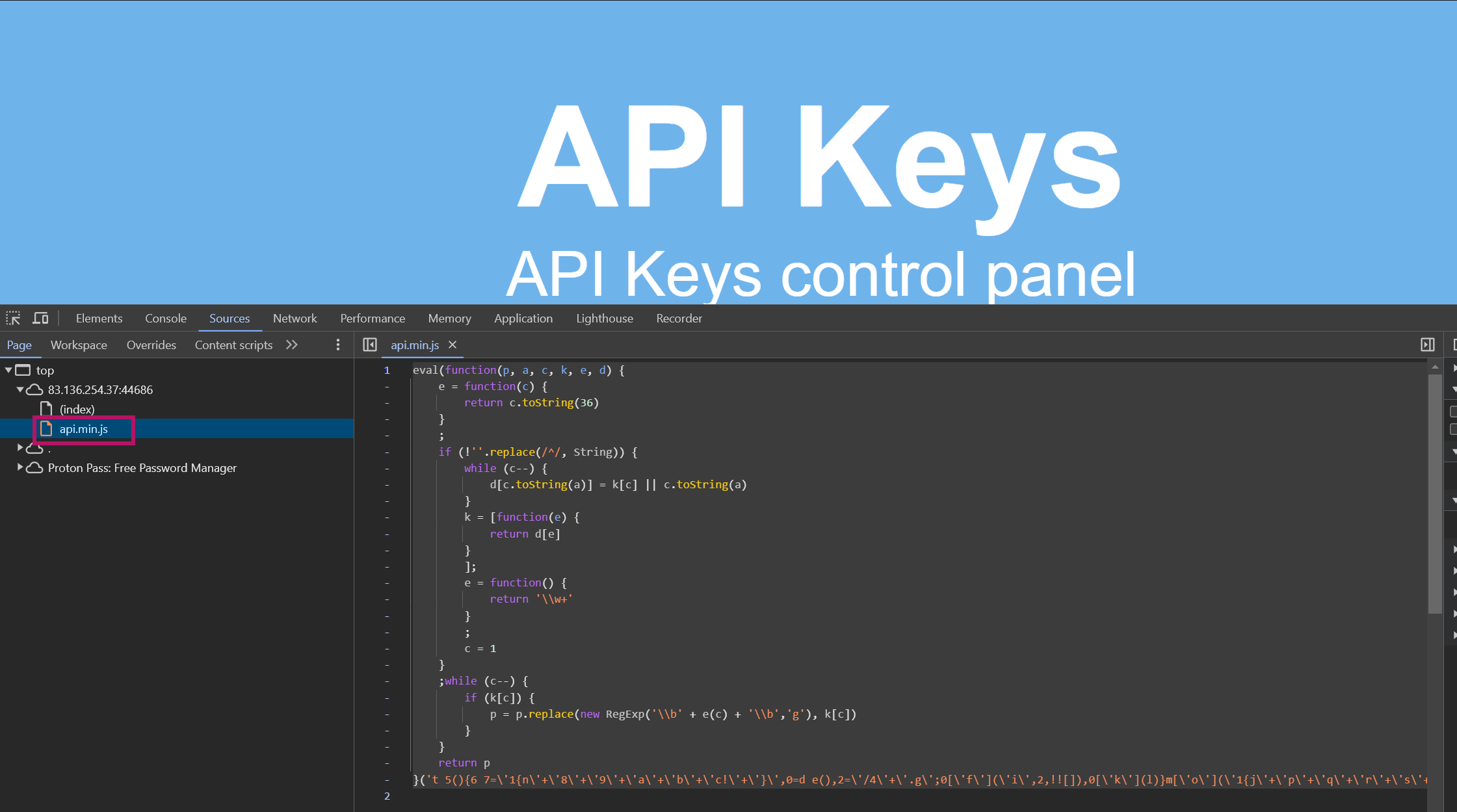
Q1: Try to study the HTML code of the webpage, and identify used JavaScript code within it. What is the name of the JavaScript file being used?
Open your preferred browser and navigate to the {Target} webpage you want to inspect.
Open the browser’s Developer Tools (usually by pressing F12 or right-clicking on the page and selecting Inspect).
In the Developer Tools window, navigate to the Sources tab.
Review the list of files under the
ScriptsorSourcessection to locate the JavaScript file(s) used by the webpage.Identify and note the name of the JavaScript file.
Answer:
api.min.js
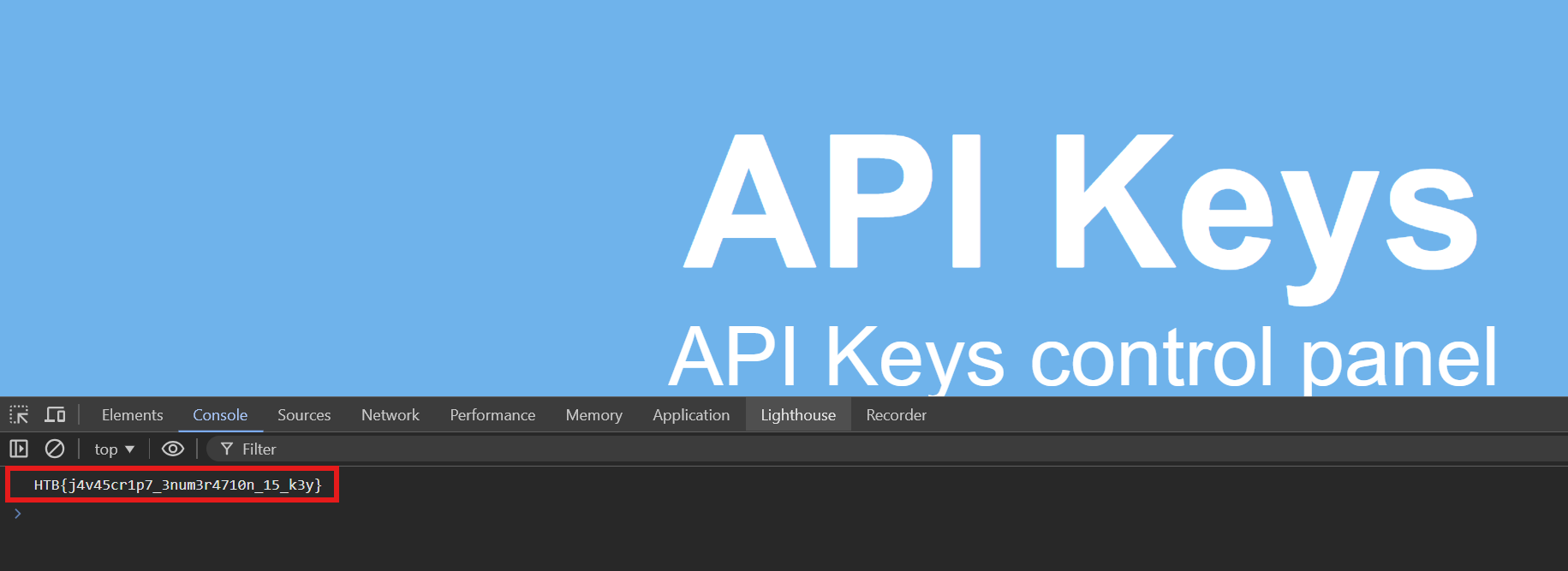
Q2: Once you find the JavaScript code, try to run it to see if it does any interesting functions. Did you get something in return?
Go to the Console tab in Developer Tools and check for any logged output. You should see the relevant information there.
Answer:
HTB{j4v45cr1p7_3num3r4710n_15_k3y}
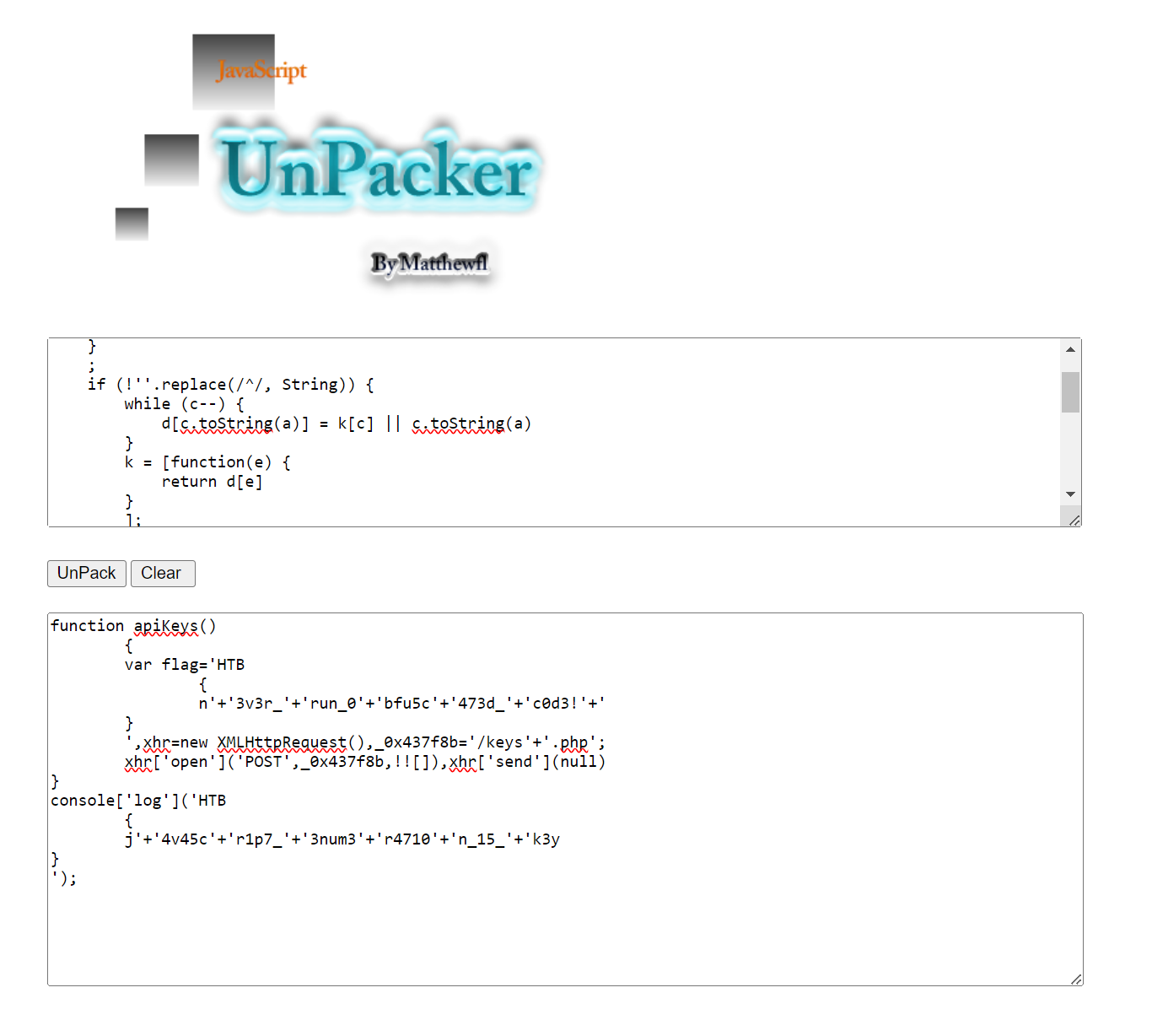
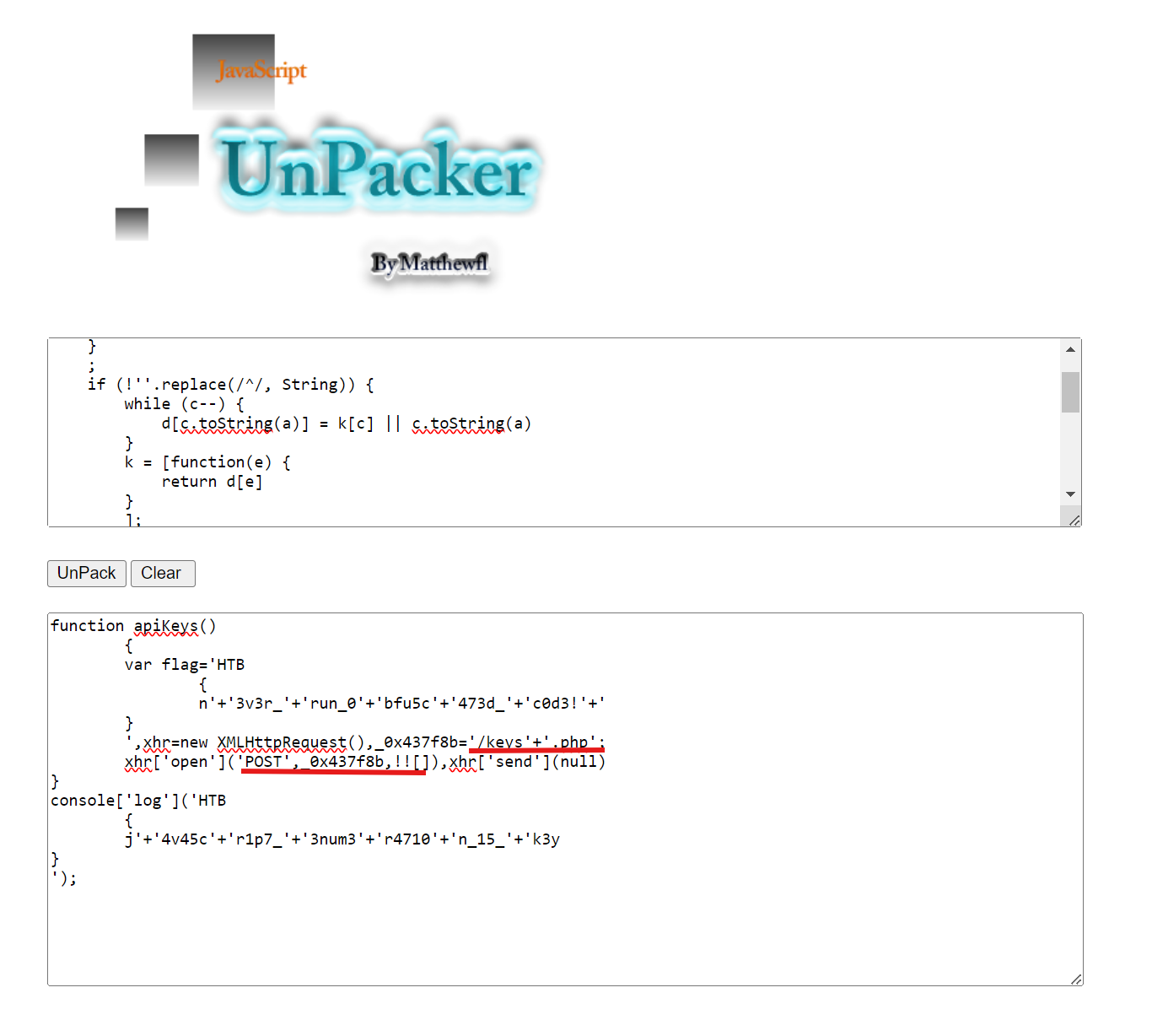
Q3: As you may have noticed, the JavaScript code is obfuscated. Try applying the skills you learned in this module to deobfuscate the code, and retrieve the ‘flag’ variable.
To deobfuscate the code, you can use Unpacker to unpack the content in api.min.js
Notice the flag variable in the code: 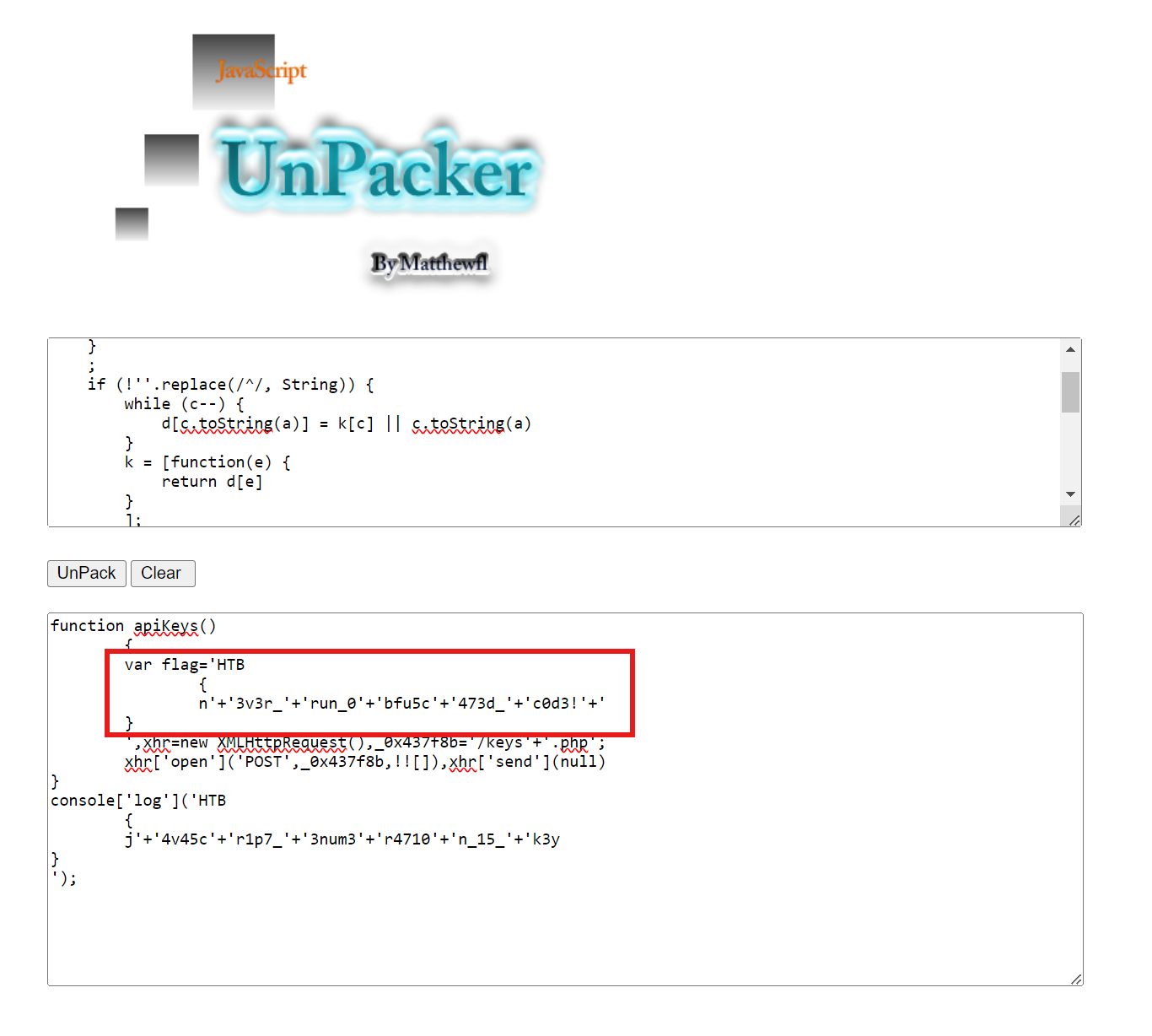
Answer:
HTB{n3v3r_run_0bfu5c473d_c0d3!}
Q4: Try to Analyze the deobfuscated JavaScript code, and understand its main functionality. Once you do, try to replicate what it’s doing to get a secret key. What is the key?
1. Analyze the Deobfuscated JavaScript:
Once you have deobfuscated the code, carefully read through it to understand the main functionality.
Look for sections that deal with generating or fetching keys, making network requests, or manipulating data. These will give you insight into how the secret key is obtained.
2. Identify the HTTP POST Request:
- After investigating the code, notice it’s making a HTTP Post request to
{Target}/keys.php
3. Replicate the Request Using Curl:
- Use the curl command to simulate the POST request manually
- Replace
{Target}with the actual target URL and ensure the correct data is sent in the request body.
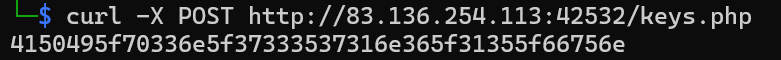
1
curl -X POST {Target}/keys.php
4. Retrieve the Secret Key:
After running the curl command, you will get a response that includes the secret key.
Answer:
4150495f70336e5f37333537316e365f31355f66756e
Q5: Once you have the secret key, try to decide it’s encoding method, and decode it. Then send a ‘POST’ request to the same previous page with the decoded key as “key=DECODED_KEY”. What is the flag you got?
1. Determine the Encoding Method:
- After receiving the secret key from the previous step, inspect it to figure out the encoding. Common encoding formats include Base64, hex, or URL encoding.
- Based on the structure of the key, you can try different decoding methods.
2. Decode the Secret Key:
Execute the following command to decrypt the payload received from the previous question.
1
echo 4150495f70336e5f37333537316e365f31355f66756e |xxd -p -r
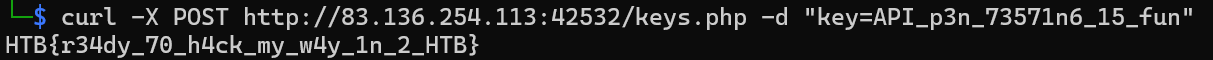
3. Send a POST Request with the Decoded Key:
- Once you have the decoded key, use curl to send another POST request to the same page ({Target}/keys.php) with the decoded key as the parameter.
1
curl -X POST http://{Target}/keys.php -d "key=API_p3n_73571n6_15_fun"
4. Retrieve the Flag:
- After sending the POST request with the decoded key, you will receive a response containing the flag.
Answer:
HTB{r34dy_70_h4ck_my_w4y_1n_2_HTB}