Hack The Box - Academy - Information Gathering Skills Assessment
Explore this detailed walkthrough of Hack The Box Academy’s Information Gathering Skills Assessment module. Learn effective techniques to perfom a successful recon.
Overview:
To complete the skills assessment, answer the questions below. You will need to apply a variety of skills learned in this module, including:
Using whois
Analysing robots.txt
Performing subdomain bruteforcing
Crawling and analysing results
Demonstrate your proficiency by effectively utilizing these techniques. Remember to add subdomains to your hosts file as you discover them.
Links:
Information Gathering - Web Edition
Information Gathering - Cheat Sheet
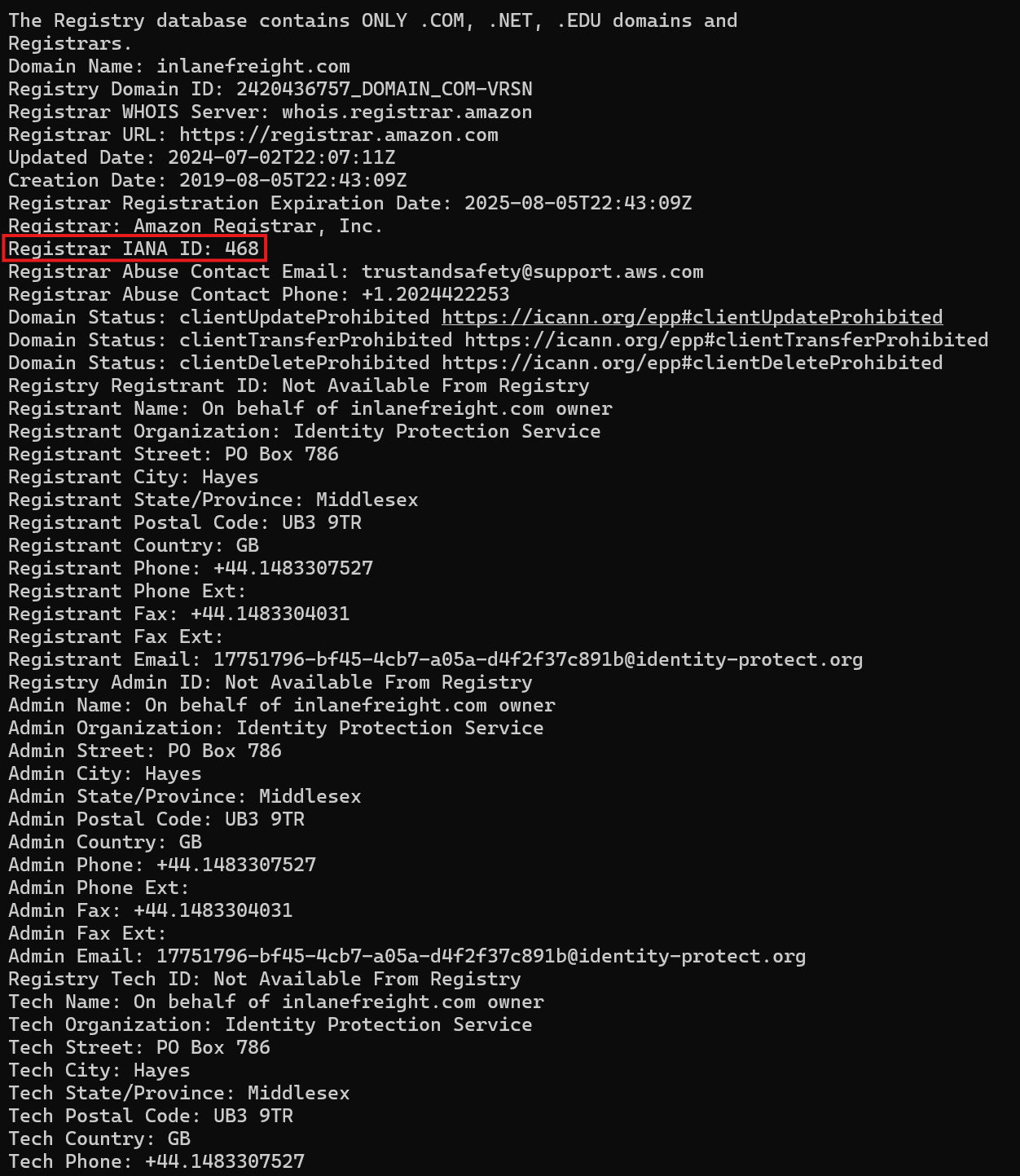
Q1: What is the IANA ID of the registrar of the inlanefreight.com domain?
Execute the bellow command:
1
whois inlanefreight.com
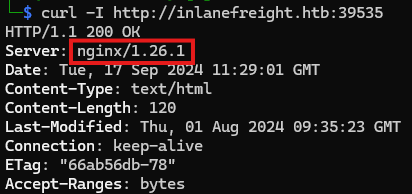
Q2: What http server software is powering the inlanefreight.htb site on the target system? Respond with the name of the software, not the version, e.g., Apache.
1. Execute the bellow command to add the Target_IP and hostname to /etc/hosts
1
sudo sh -c 'echo "{TARGET_IP} inlanefreight.htb" >> /etc/hosts'
2. Execute the bellow command to retrieve the server banner, revealing the web server software and version number:
1
curl -I http://inlanefreight.htb:{PORT}
Q3: What is the API key in the hidden admin directory that you have discovered on the target system?
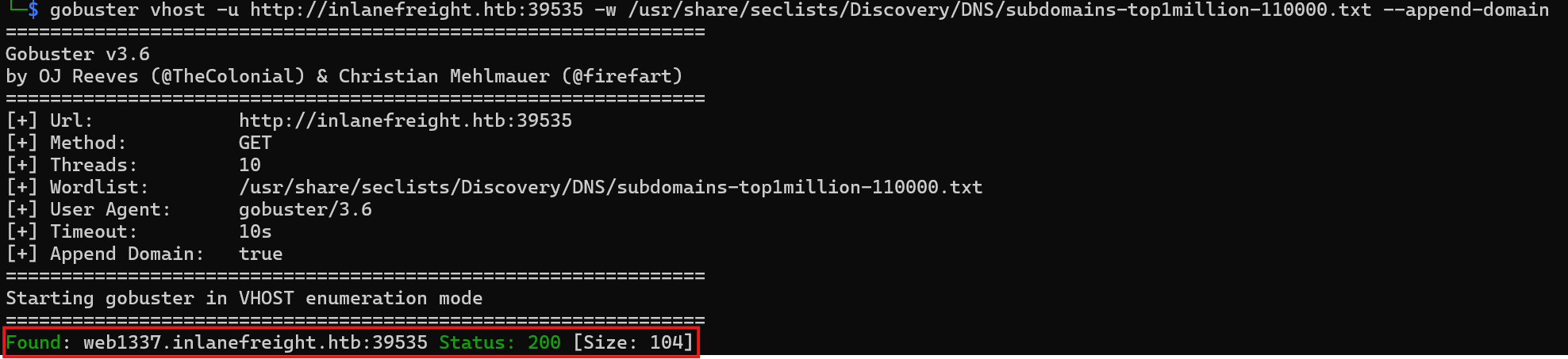
1. Execute the below command to find sub domains for inlanefreight.htb
1
gobuster vhost -u http://inlanefreight.htb:{PORT} -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
2. Execute the below command to add web1337 to /etc/hosts
1
sudo sh -c 'echo "{TARGET_IP} web1337.inlanefreight.htb" >> /etc/hosts'
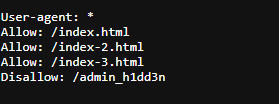
3. Navigate to the robots.txt http://web1337.inlanefreight.htb:{PORT}/robots.txt file and look for the Disallow directory:
4. Execute the below command to enumerate directories / files
1
ffuf -u http://web1337.inlanefreight.htb:39535/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt:FUZZ -e .html -v
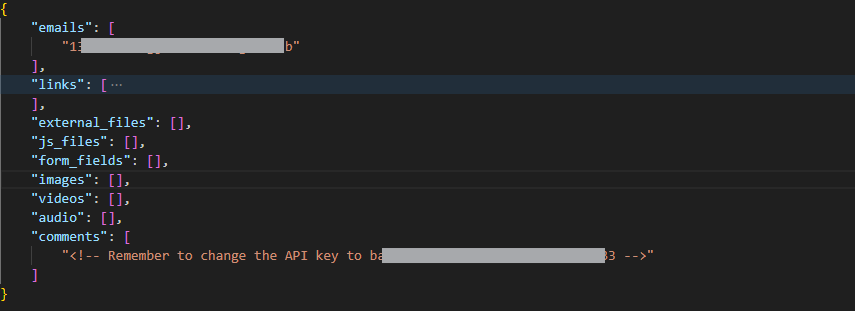
Q4: After crawling the inlanefreight.htb domain on the target system, what is the email address you have found? Respond with the full email, e.g., mail@inlanefreight.htb. & Q5: What is the API key the inlanefreight.htb developers will be changing too?
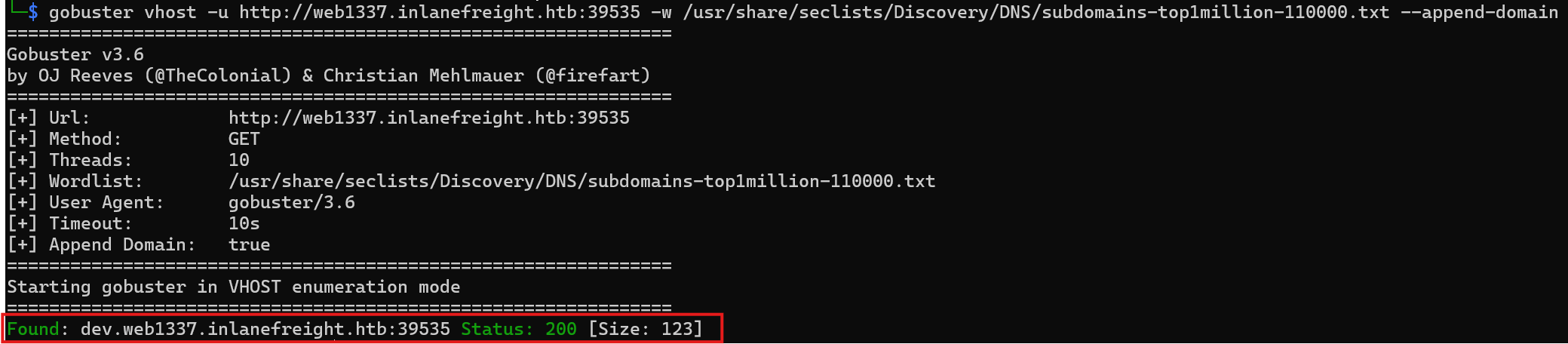
1. Execute the below command to find sub domains for web1337.inlanefreight.htb
1
gobuster vhost -u http://inlanefreight.htb:{PORT} -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
2. Execute the below commands to install Scrapy and ReconSpider
1
pip3 install scrapy
1
wget -O ReconSpider.zip https://academy.hackthebox.com/storage/modules/144/ReconSpider.v1.2.zip
1
unzip ReconSpider.zip
1
python3 ReconSpider.py http://dev.web1337.inlanefreight.htb:{PORT}
3. Review the results
1
cat results.json
This post is licensed under CC BY 4.0 by the author.