Explore this detailed walkthrough of Hack The Box Academy’s Attacking Web Applications with Ffuf module. Learn effective techniques to leverage Ffuf for web application attacks.
Overview:
You are given an online academy’s IP address but have no further information about their website. As the first step of conducting a Penetration Test, you are expected to locate all pages and domains linked to their IP to enumerate the IP and domains properly.
Finally, you should do some fuzzing on pages you identify to see if any of them has any parameters that can be interacted with. If you do find active parameters, see if you can retrieve any data from them.
Links:
Attacking Web Applications with Ffuf
Attacking Web Applications with Ffuf - Cheat Sheet
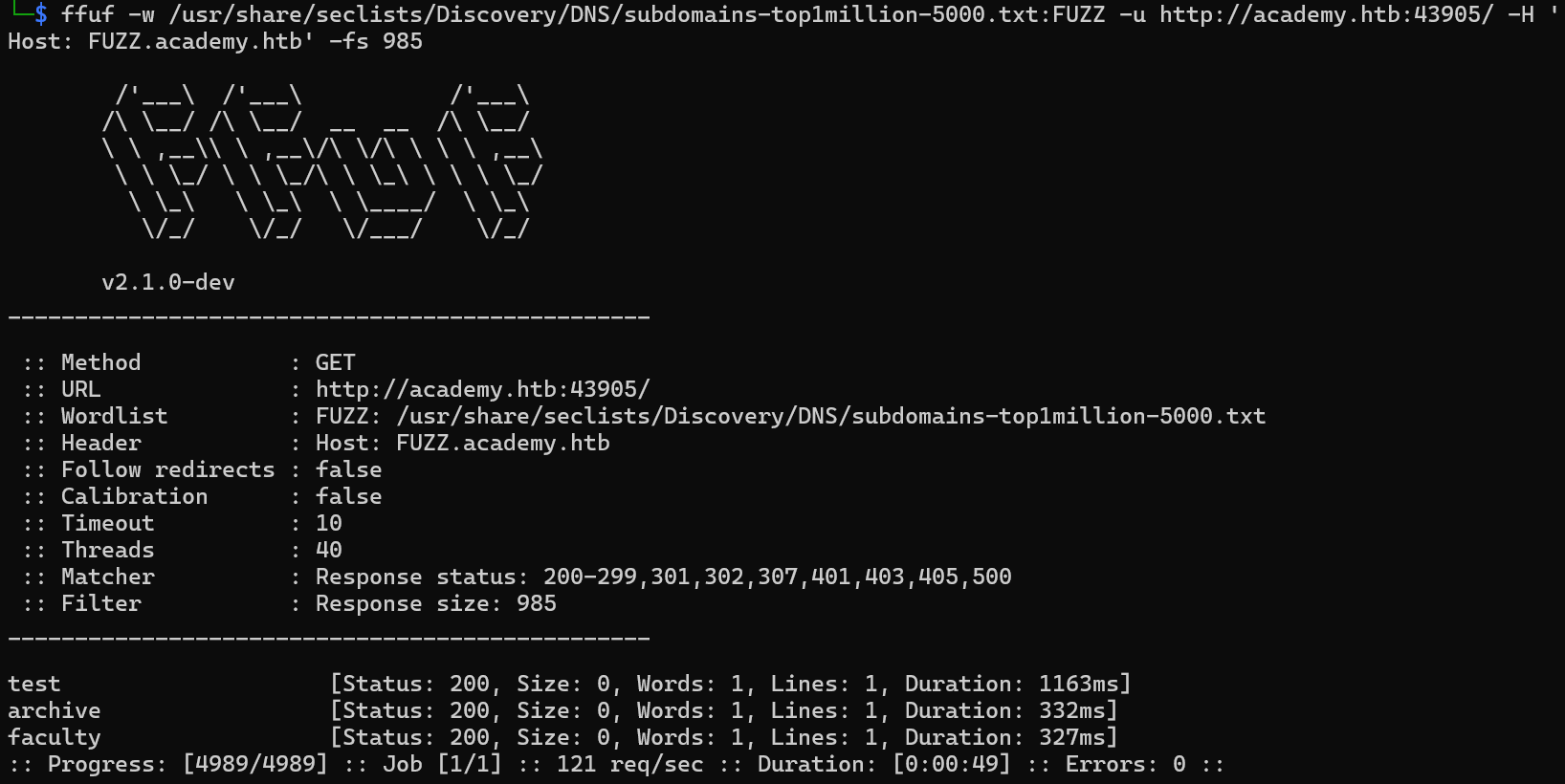
Q1: Run a sub-domain/vhost fuzzing scan on ‘*.academy.htb’ for the IP shown above. What are all the sub-domains you can identify? (Only write the sub-domain name)
Add academy.htb to /etc/hosts: Replace {TARGET_IP} with the actual target IP address and execute the command:
1
| sudo sh -c 'echo "{TARGET_IP} academy.htb" >> /etc/hosts'
|
Run the Subdomain/Vhost Scan: Execute the following command to start the scan.
1
| ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://academy.htb:{PORT}/ -H 'Host: FUZZ.academy.htb' -fs 985
|
After running the command, ffuf will scan for subdomains and should list any found subdomains under *.academy.htb.
The results will include valid subdomains that respond with a different size than 985 bytes (which is what -fs 985 is filtering out)
Answer:
test, archive, faculty
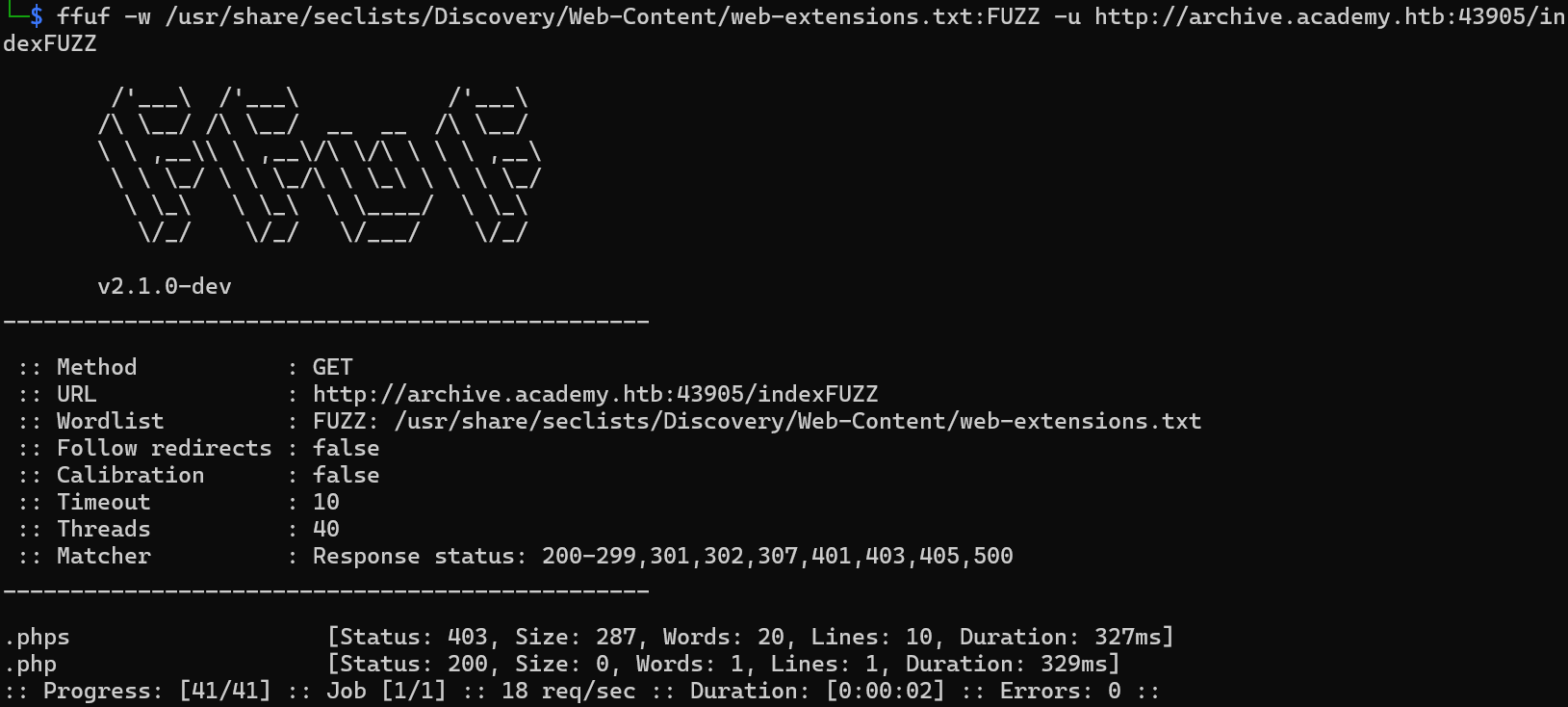
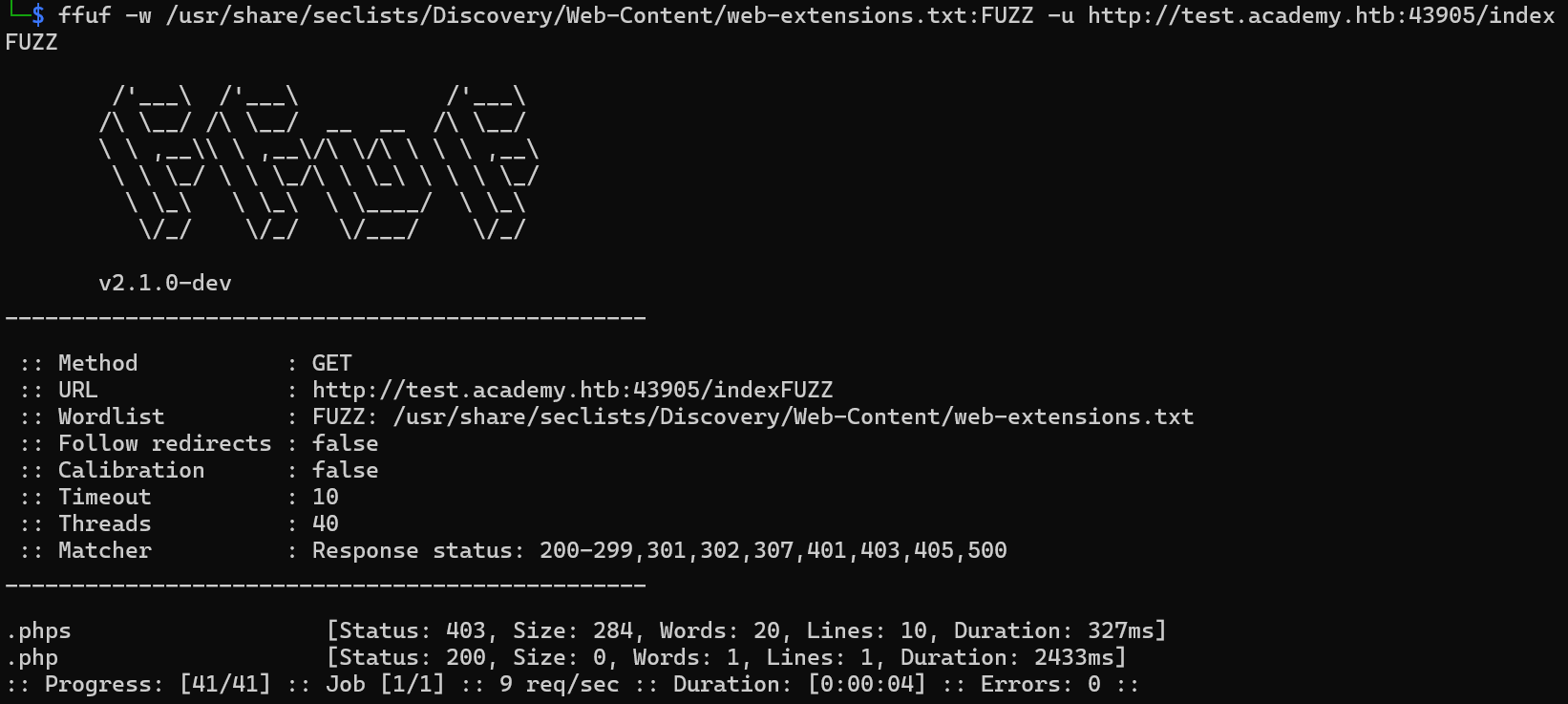
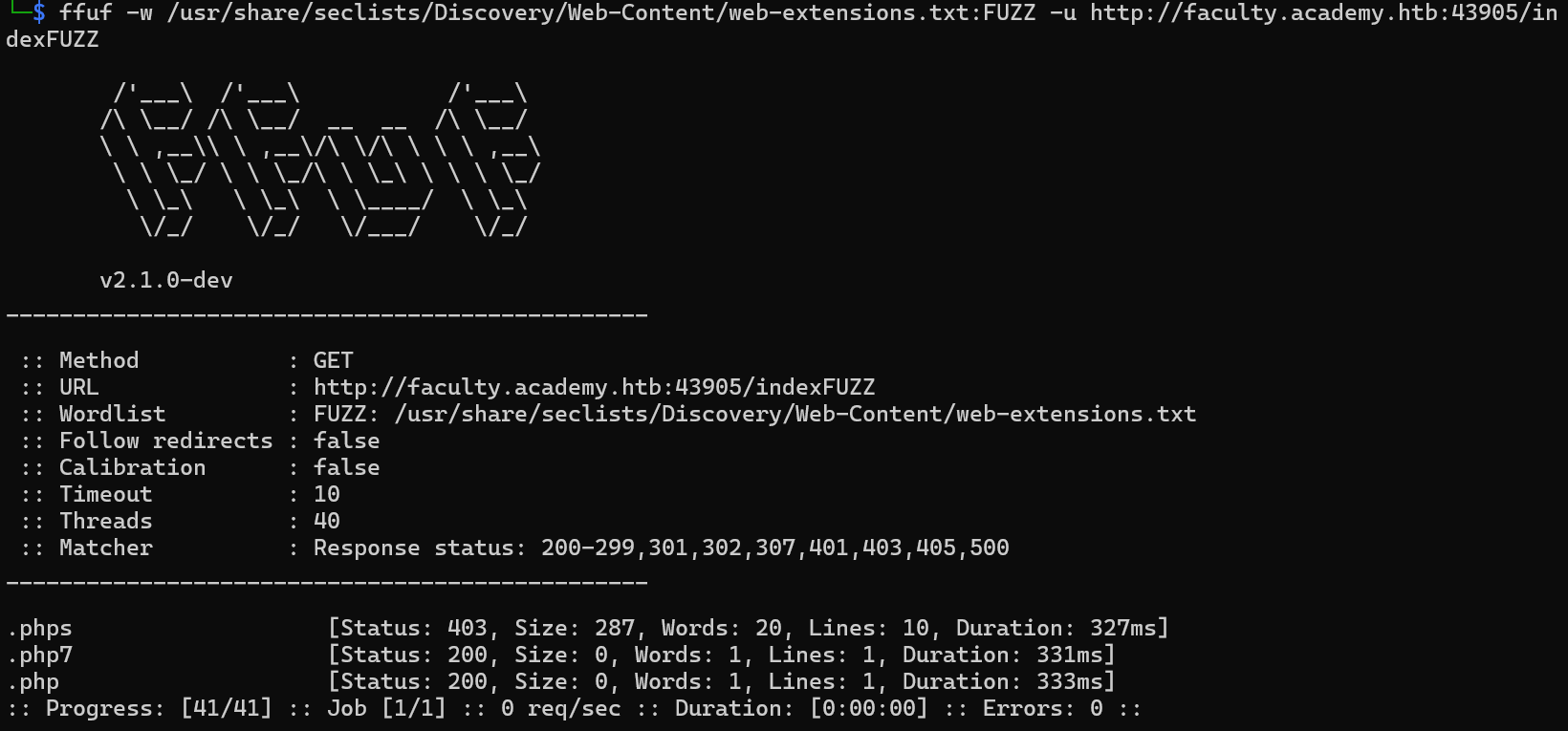
Q2: Before you run your page fuzzing scan, you should first run an extension fuzzing scan. What are the different extensions accepted by the domains?
1. Add the Subdomains to /etc/hosts: Execute the following commands, replacing {TARGET_IP} with the actual target IP address:
1
| sudo sh -c 'echo "{TARGET_IP} acrhive.academy.htb" >> /etc/hosts'
|
1
| sudo sh -c 'echo "{TARGET_IP} test.academy.htb" >> /etc/hosts'
|
1
| sudo sh -c 'echo "{TARGET_IP} faculty.academy.htb" >> /etc/hosts'
|
2. Run Extension Fuzzing Scans: You will run extension fuzzing scans for each subdomain using ffuf
For archive.academy.htb:
1
| ffuf -w /usr/share/seclists/Discovery/Web-Content/web-extensions.txt:FUZZ -u http://archive.academy.htb:{PORT}/indexFUZZ
|
For test.academy.htb:
1
| ffuf -w /usr/share/seclists/Discovery/Web-Content/web-extensions.txt:FUZZ -u http://test.academy.htb:{PORT}/indexFUZZ
|
For faculty.academy.htb:
1
| ffuf -w /usr/share/seclists/Discovery/Web-Content/web-extensions.txt:FUZZ -u http://faculty.academy.htb:{PORT}/indexFUZZ
|
Answer:
php, phps, php7
Q3: One of the pages you will identify should say ‘You don’t have access!’. What is the full page URL?
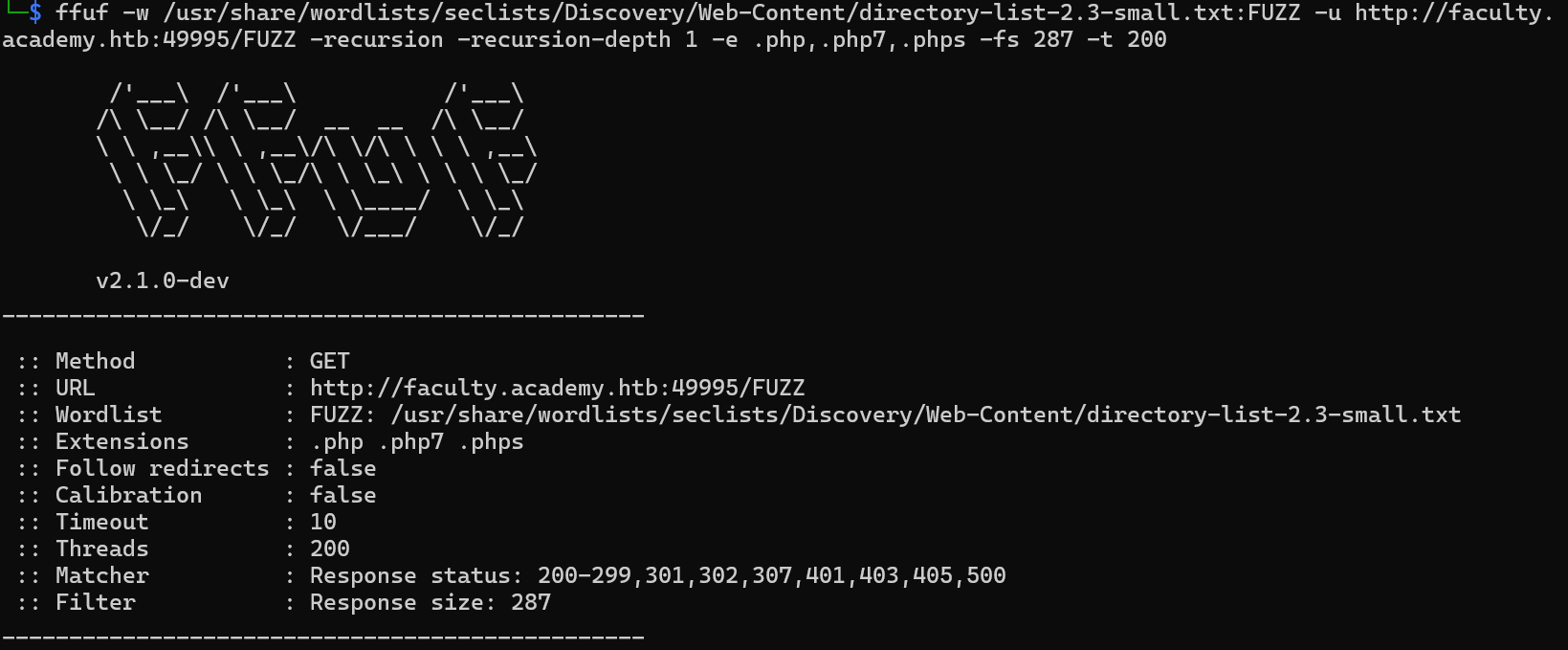
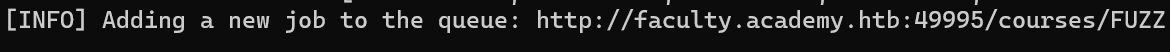
Execute the following command to start the directory fuzzing
1
| ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -u http://faculty.academy.htb:{PORT}/FUZZ -recursion -recursion-depth 1 -e .php,.php7,.phps -fs 287 -t 200
|
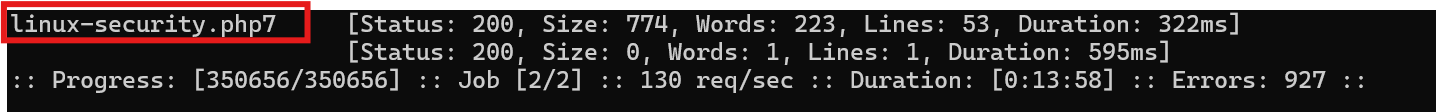
Answer:
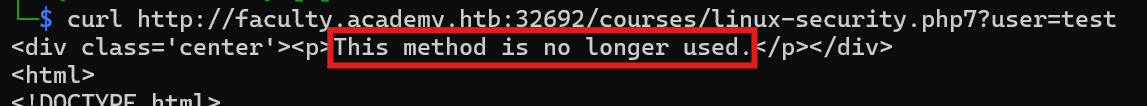
http://faculty.academy.htb:PORT/courses/linux-security.php7
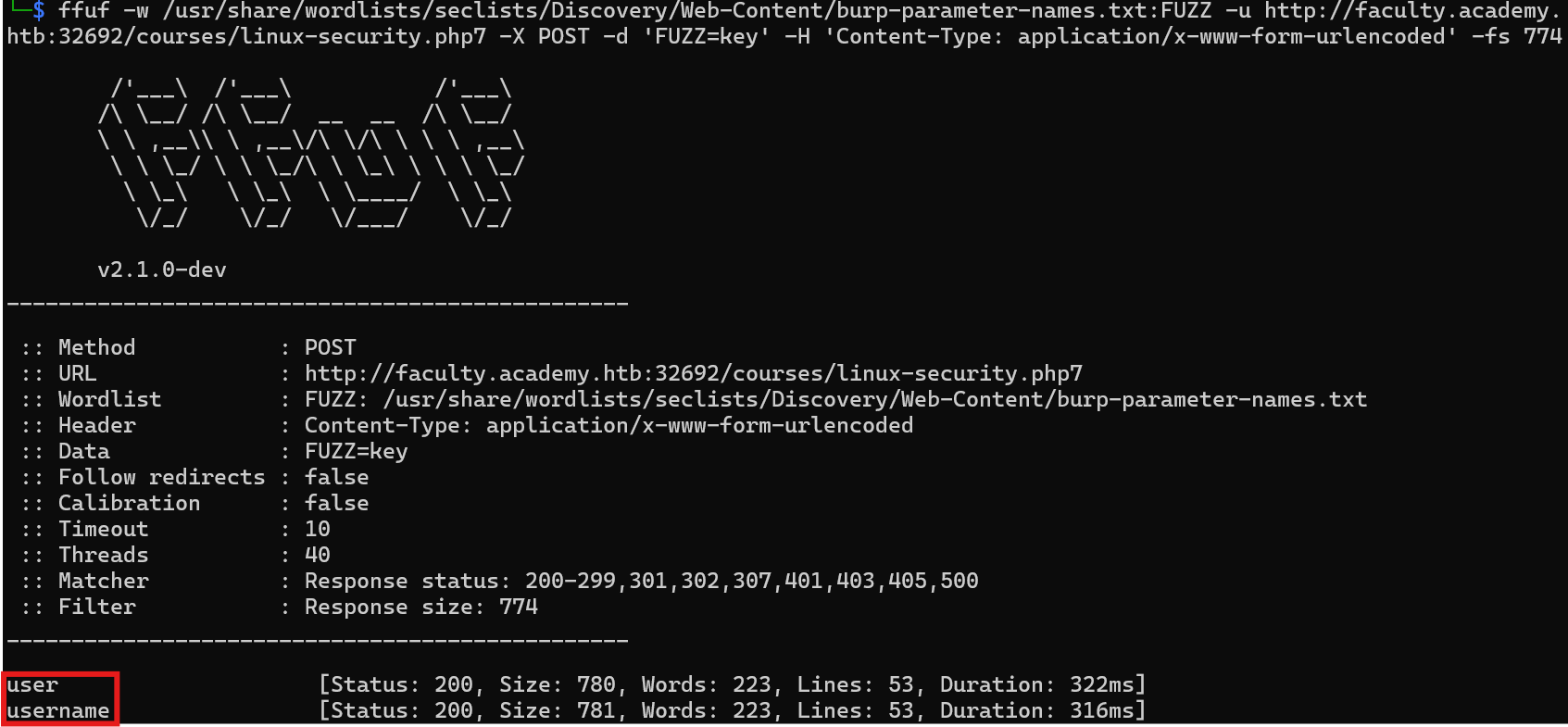
Q4: In the page from the previous question, you should be able to find multiple parameters that are accepted by the page. What are they?
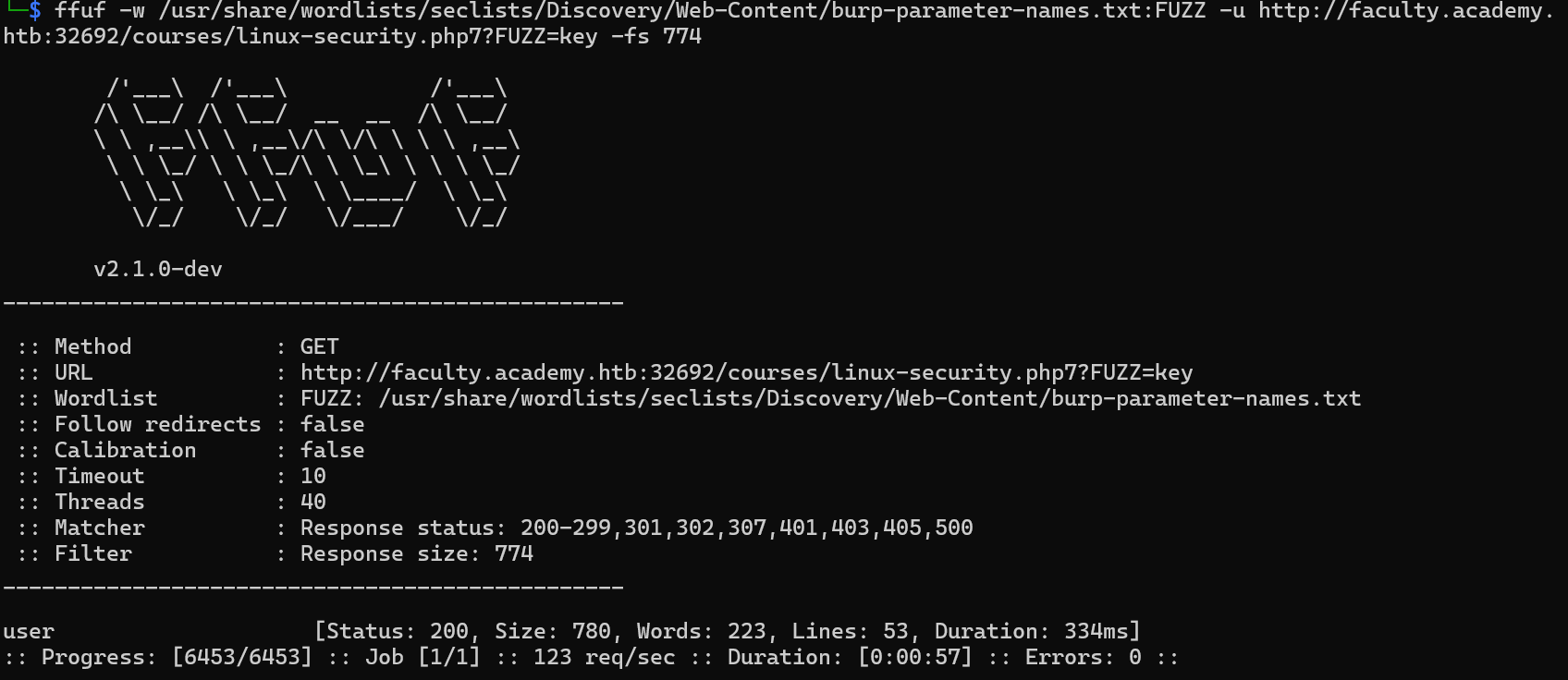
Execute the following command to start the parameter fuzzing using GET
1
| ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt:FUZZ -u http://faculty.academy.htb:{PORT}/courses/linux-security.php7?FUZZ=key -fs 774
|
Execute the following command to start the parameter fuzzing using POST
1
| ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt:FUZZ -u http://faculty.academy.htb:{PORT}/courses/linux-security.php7 -X POST -d 'FUZZ=key' -H 'Content-Type: application/x-www-form-urlencoded' -fs 774
|
Answer:
user,username
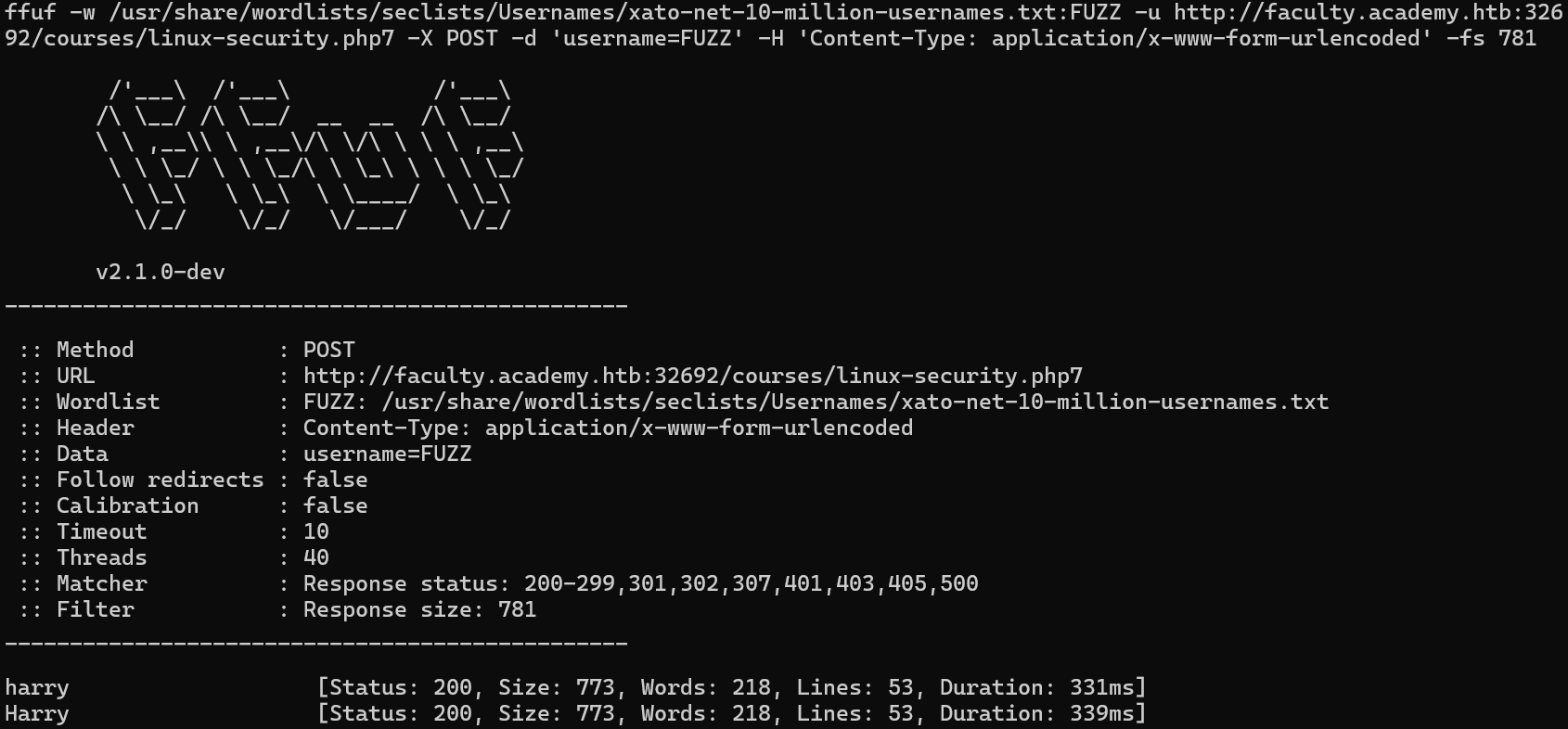
Q5: Try fuzzing the parameters you identified for working values. One of them should return a flag. What is the content of the flag?
Execute the following command to enumerate usernames:
1
| ffuf -w /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt:FUZZ -u http://faculty.academy.htb:{PORT}/courses/linux-security.php7 -X POST -d 'username=FUZZ' -H 'Content-Type: application/x-www-form-urlencoded' -fs 781
|
Execute the following command retrieve the flag:
1
2
| curl http://faculty.academy.htb:{PORT}/courses/linux-security.php7 -X POST -d 'username=harry' -H 'Content-Type: application/x-www-form-urlencoded'
|
Answer:
HTB{w3b_fuzz1n6_m4573r}